Cyber Terrorism: What It Is and How It’s Evolved

Tables of Contents
In May 2021, gasoline supplies to the East Coast of the United States were reduced by 45%, causing cars to line up for blocks to fill their tanks. The cause: a cyberattack on the Colonial Pipeline that carried gas and other fuels to the East Coast from Texas. The attack was traced to the international ransomware group DarkSide, as the Guardian reports.
In June 2021, meat supplies were threatened by a ransomware attack on meat processing factories owned by JBS, a company that supplies more than one-fifth of the beef consumed in the U.S., as explained in the Guardian. JBS, which is headquartered in Brazil, also experienced disruptions to operations in Australia and other countries. This was one of several cyberattacks in 2021 thought to have originated in Russia.
A hacking campaign suspected of being sponsored by China has targeted Microsoft’s Exchange email server for corporations. The New York Times reports that the attackers struck in January 2021 and escalated the attacks weeks later. Security analysts believe that tens of thousands of accounts may have been compromised. Microsoft estimates that 30,000 Exchange customers were likely affected by the data breach, but the company said it did not know how extensive the data leak was.
These examples illustrate the dangers posed by cyber terrorism to governments and organizations around the world. Cyber terrorism and other cyberattacks cost governments, businesses, and individuals more than $1 trillion each year, according to computer security firm McAfee. Cybersecurity Ventures forecasts that the cost of cyber crime of all types will reach $10.5 trillion annually by 2025.
Combating cyber terrorism and cyber crime requires understanding how cyber terrorists act, what motivates them, and how to prevent their attacks. This guide looks at the evolution of cyber terrorism, highlights examples of cyber terrorism and cyberattacks, and offers tips for thwarting cyberattacks.
What is cyber terrorism?
Cyber terrorism is defined by researchers Jordan Plotnek and Jill Slay as a premeditated attack or the threat of such an attack by nonstate actors intending to use cyberspace to cause physical, psychosocial, political, economic, ecological, or other damage. The goal of the cybercriminals is to induce fear or coerce government or nongovernment bodies to act in a way that furthers the criminals’ social, financial, or ideological objectives.
A cyber terrorism taxonomy includes six elements:
- An actor or actors with three unique attributes: nonstate, terrorist, and clandestine
- A motive, which may be ideological, social, economic, or political
- An intent to induce or coerce some action, effect change, further objectives, or cause interference
- The means to commit the act, which includes using a computer and network to access cyberspace and cross borders to commit acts of cyber warfare or crimes, including cyberattacks and threats of attacks
- An effect, most commonly violence, service disruptions, physical damages, psychosocial impacts, economic damages, or data breaches
- A target, most commonly civilians, information and communication technology (ICT), data sources, government agencies, nongovernment organizations, or physical infrastructure
Major cyber terrorism attacks and attempts
Attacks on computer networks, data stores, communication systems, or command-and-control systems are committed using a variety of methods and for many different purposes. While many cyber terrorism attacks are widely reported, most cyberattacks and attempts to breach computer networks receive little or no notice.
These are some of the most damaging cyber terrorism attacks and attempts in recent years.
- Information technology firm SolarWinds was the victim of a cyberattack that went undetected for several months, as Business Insider reports. Hackers widely believed to be operating in Russia were able to spy on private companies, including security firm FireEye, and many government agencies. In April 2021, the U.S. government implemented sanctions on Russia as a result of the attack.
- Insurance firm CNA Financial reportedly paid hackers $40 million in March 2021 after being the victim of a ransomware attack that locked the company’s computer networks and stole data, as reported in Bloomberg. The attack did not breach the majority of policyholder data, according to the company.
- IT services firm Kaseya announced in July 2021 that it had been the victim of a cyberattack by the REvil ransomware, as explained on ZDNet. The attack breached the company’s supply chain software, resulting in ransomware attacking between 800 and 1,500 of the small managed service healthcare providers that are among Kaseya’s customers.
- Mobile service provider T-Mobile announced in August 2021 that it was the victim of a cyberattack that compromised the personal information of 13 million customers and an additional 40 million people who had applied for an account with the company, as Fortune reports. The attack marks the fourth time in as many years that T-Mobile has had its customer data hacked: twice in 2020 and once in 2018, when the data of about 2.5 million customers was exposed.

Cyber terrorism targets and attackers’ motivation
According to the Annual Threat Assessment of the U.S. Intelligence Community released on April 9, 2021, the greatest cyber threats against U.S. interests are posed by China and Russia. In addition, countries such as Iran continue to harbor and support Hezbollah and other terrorist groups. The cyber capabilities of groups such as ISIS (the Islamic State of Iraq and Syria) and Al Qaeda remain threats despite recent leadership losses, according to the report.
In addition to ICT and physical infrastructure, cyber terrorism attacks target managed service providers and popular business software such as Microsoft Office. The goal of the attacks is to steal information or sabotage the systems they infect. IBM lists the most common targets of cyberattacks:
- Confidential information from U.S. government agencies
- Sensitive personal data
- Access to IT infrastructure
- Financial payment systems
- Trade secrets and other intellectual property
- Email addresses, user IDs, and passwords
- Customer databases and financial data
- Client lists
Security vendor Checkpoint Software identifies four trends in cyberattacks in its midyear 2021 report:
- An increase in attacks on supply chain software: The two most common forms of attack are those designed for well-defined targets looking for holes in their list of suppliers, and those that leverage holes in large distribution networks to use software supply chains to target as many victims as possible.
- Phishing email attacks become more evasive: Social engineering techniques continue to gain in sophistication, finding new ways to bypass email security. The attackers frequently use blackmail to extort money from victims, or they may elude detection by impersonating someone the victim knows.
- More attacks on data stored in the public cloud: As more organizations and individuals take advantage of the low cost and security of public cloud services, cyber terrorists and cybercriminals target these systems in their attacks. A primary source of cloud data breaches is misconfigured cloud environments.
- Attacks on mobile devices: Malware designed to attack computer networks and computer users are being adapted to strike people who use mobile devices. Checkpoint Software notes a 50% increase in the penetration of banking malware in mobile networks between 2018 and 2019. The malware has been found in mobile apps, where it can steal payment data, credentials, and the victim’s funds.
History of cyber terrorism
Small Wars Journal notes that the term “cyber terror” was coined in the 1980s by Barry C. Collin, a research fellow at the Institute for Security and Intelligence. Collin defined the term as “the convergence of cybernetics and terrorism”; the goal of causing fear and widespread panic has always been at the heart of cyber terror attacks.
The first computer worm transmitted over the internet was the Morris Worm, created in 1988 by Robert Tappan Morris, a student at Cornell University, as the tech site ARN explains. The worm was not intended to be malicious, but an error in its code caused it to become a virus that replicated rapidly and ultimately infected about 6,000 computers. The Morris Worm is estimated to have caused as much as $100 million in damage.
Terrorists soon took advantage of malicious software such as worms to promote their political, social, and economic ends. These are among the earliest events in the history of cyber terrorism:
- In March 1999, the Melissa virus “began spreading like wildfire” across the internet, according to the FBI. Melissa targeted Microsoft’s Word word processing software and Outlook email software to automatically send messages to the first 50 people in the victim’s contact list. The virus was created by David Lee Smith and was intended not for financial gain but to cause havoc. Melissa damaged email servers at hundreds of corporations worldwide, temporarily knocking out access to about 1 million email accounts.
- In May 2007, government agencies and private businesses in Estonia were the target of massive, weeks-long cyberattacks after the government removed some Russian World War II memorabilia from the city of Tallinn. The distributed denial-of-service (DDOS) attacks caused Estonia’s largest bank to shut down, resulting in about $1 million in damage. Analysts suspect that the Russian Federation supported the attacks, although Russia denies the charge.
- In August 2013, a hacker group called the Syrian Electronic Army took over the websites of the New York Times, Huffington Post, and Twitter by breaching the network of MelbourneIT, an Australian internet service provider that manages corporate domain names. The group had previously targeted the websites of the Washington Post, CNN, and Time. The motivation for the attack was reprisal for criticism of Syrian president Bashar al-Assad.
- In May 2017, the WannaCry ransomware attack struck Microsoft Windows systems, demanding $300 in Bitcoin (later increased to $600) from victims to regain access to their computer files. Months before the attack, Microsoft had issued a patch for the vulnerability exploited by WannaCry, but many users had not updated their system to protect against the attack. A fault in the code of the virus prevented victims from recovering their files even if they paid the ransom.
Cyber terrorism attacks have become more sophisticated
A significant security trend in recent years is the escalation of the threats posed by cyber terrorism to governments, businesses, and individuals as new technologies are developed. Government Technology reports that the surge in cyberattacks that began in 2020 is continuing in 2021 as attacks become more frequent and more damaging.
- On February 5, 2021, hackers used a hole in an old version of Windows to break into the network of a Florida water treatment plant and boost the levels of sodium hydroxide (lye) to lethal levels. The attack was thwarted before any damage could be done by an operator who noticed the change and corrected the levels. However, the attack highlights the vulnerability of water systems and other vital infrastructure in the U.S.
- The FBI now considers ransomware as grave a danger to U.S. interests as terrorism in the aftermath of the attacks of Sept. 11, 2001, as the New York Times reports. The agency is currently analyzing 100 different software variants used in ransomware attacks by criminal gangs and by groups operating within China and Russia. Analysts expect more damaging attacks to target critical infrastructure in the U.S.
- In October 2021, the U.S. National Security Agency (NSA) warned businesses against using wildcard Transport Layer Security (TLS) digital encryption certificates to guard against a new type of malware called ALPACA (Application Layer Protocols Allowing Cross-Protocol Attack). ALPACA infiltrates hardened web applications via non-HTTP services that use a certificate identical to or similar to a TLS certificate. The technique tricks web servers into responding to encrypted HTTP requests using unencrypted protocols.
Resources on the history of cyber terrorism
- Forbes, “Russia Has Carried Out 20 Years of Cyber Attacks That Call for an International Response” — The country’s attacks on U.S. interests began in 1996 with the release of the Moonlight Maze cyber espionage campaign that targeted the Department of Energy, NASA, and other government agencies.
- Security, “Notorious Cybersecurity Attacks in History and How to Prevent Them” — This article describes cyberattacks including those targeting NASA and the U.S. Department of Defense in 1999, and the World Health Organization (WHO), the National Institutes of Health (NIH), and the Gates Foundation in 2020.
- Center for Strategic & International Studies, “Significant Cyber Incidents Since 2006” — This timeline includes incidents that have been linked to cyber terrorists and criminals operating in China, Iran, Brazil, Russia, and North Korea.
Examples of cyber terrorism
According to IBM, the average cost of a data breach to organizations increased from $3.86 million in 2020 to $4.24 million in 2021. Recent cyber terrorism attacks have been lodged against the Robinhood online trading platform, resulting in the exposure of personal information about its clients, and against the banking industry, which saw a 1,318% increase in ransomware attacks in just one year, as Trend Micro reports.
According to Trend Micro, attacks on business email systems increased by 4% in the first quarter of 2021, and 164 malicious apps related to COVID-19 scams were detected in the period.
These are the most common examples of cyber terrorism currently used by cybercriminals.
Hacktivism and cyber terrorism
Hacktivism is an attack on a computer system by a group with political or social motives. Examples of hacktivism and cyber terrorism include groups such as Anonymous, which promotes what are considered “leftist-libertarian ideals,” and the former LulzSec, which was broken up in 2011 after a series of high-profile attacks (and subsequent arrests), including the infamous attacks on Sony Pictures Entertainment.
Among the methods used by hacktivist groups are web defacement (sometimes referred to as internet graffiti), denial-of-service (DOS) attacks designed to inundate web servers with traffic, and doxxing — exposing the personal information of police officers and others targeted by the attackers for political or social reasons. While many hacktivists attempt to minimize actual damage when calling attention to their cause, others have attempted to incite violence and encourage real-world protests against their targets.
Cyber warfare and cyber terrorism
Cyber warfare occurs when states or international organizations perpetrate hostile acts against other states using cyberspace as a battleground. The acts are committed using malware and other technologies to target the computer systems of governments and businesses. Such attacks constitute an act of war because they are acts of aggression by one state against another.
Cyber warfare and cyber terrorism are linked through their common goals: to destabilize enemy states or compromise their physical and/or digital infrastructure. Examples of cyber warfare include the 2010 Stuxnet worm that disabled Iran’s nuclear infrastructure (believed to have been developed by the U.S. with Israeli support), the 2015 breach of the U.S. Office of Personnel Management by China, and Russia’s interference in the 2016 U.S. presidential election.
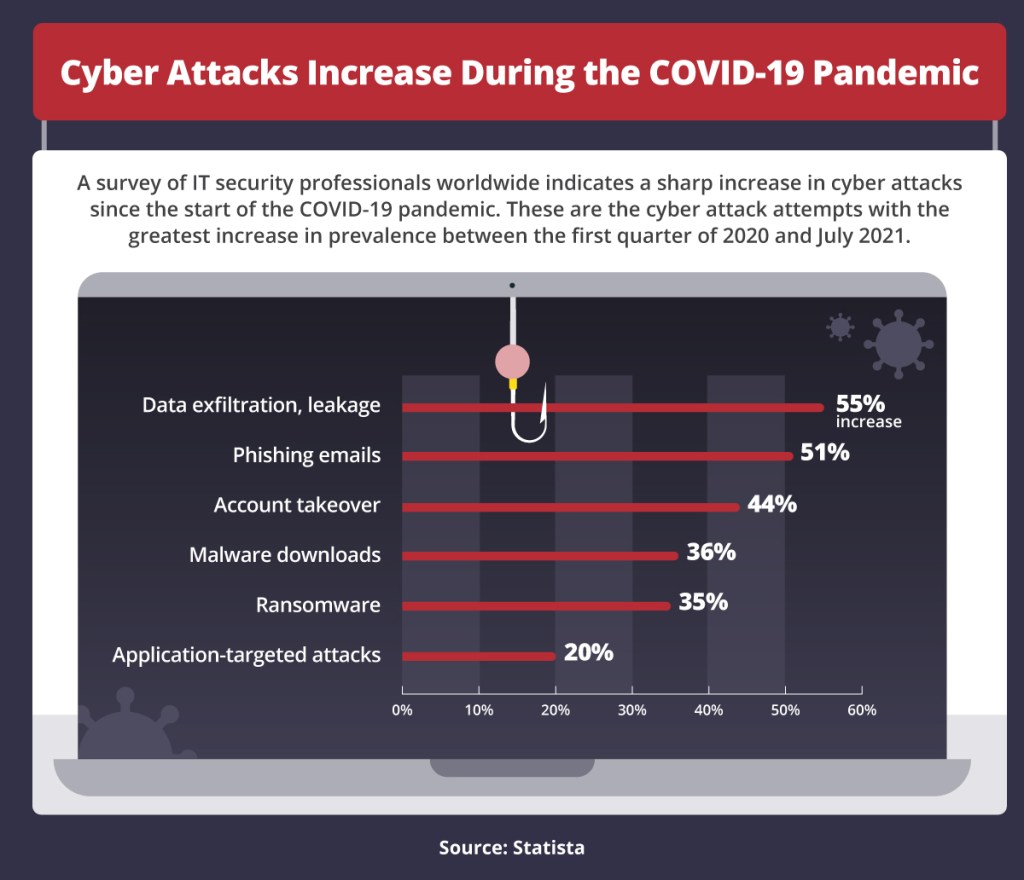
Types of cyber terrorism attacks
Criminal governments and nonstate actors use many types of cyber terrorism attacks to access and corrupt government, military, and business databases; steal sensitive information for monetary gain; and extort money from governments and businesses, among other purposes. These are the most common methods used in cyberattacks.
Malware
Malware is malicious software that gains unauthorized access to computers and networks, and damages or disrupts them with the goal of causing harm to the victim and/or financial gain for the attacker. Among the common delivery mechanisms for malware are phishing emails, email attachments, malicious ads, bogus software installation programs, and infected USB drives and applications.
Types of malware include ransomware, viruses that perform some malicious action when opened, worms that copy themselves on the host machine and from machine to machine, and spyware that tracks the victim’s actions, records communications, and downloads personal files.
Phishing
Phishing is an attack disguised as an email to trick the recipient into launching malware that collects personal information or does other damage. This is the most common method for cyber terrorists and other criminals to infect the machines and networks of their victims.
CRN reports that the FBI’s Internet Crime Complaint Center (ICCC) recorded twice as many phishing incidents in 2020 as in the previous year. A recent trend in cybercrime is for attackers to focus on creating the ransomware payload and outsourcing the phishing component to a third party, which is called an “initial access broker.”
Ransomware
Ransomware is malicious software that locks victims out of their computer files and blocks other resources, releasing them only after the victims pay a ransom, typically in the form of a cryptocurrency such as Bitcoin. Ransomware is usually delivered via a phishing attack or more sophisticated spear phishing attempt, which uses social engineering to trick the victim into opening the file and launching the attack.
The security vendor BlackFog identifies the most frequent targets of ransomware attacks:
- Government: 47 attacks from January to October 2021
- Education: 35 attacks
- Healthcare: 33 attacks
- Services: 28 attacks
- Technology: 27 attacks
- Manufacturing: 22 attacks
- Retail: 13 attacks
- Utilities: eight attacks
In addition to the ransomware attacks on Colonial Pipeline, Kaseya, and CNA Financial, noteworthy ransomware incidents two other noteworthy ransomware incidents occurred in 2021:
- Ireland’s Health Service Executive refused to pay the attackers’ $20 million ransom demand. The attack disrupted healthcare services in the country for several weeks.
- German chemical distributor Brenntag paid a $4.4 million ransom demand to the criminal gang DarkSide. The attackers encrypted devices on the company’s network and stole unencrypted files.
Man-in-the-middle attacks
A man-in-the-middle attack is similar to spyware in that the attacker lurks on the victim’s network or computer, tracking and recording all the information that the person accesses or transmits. The software captures personal identification numbers, passwords and user IDs, and financial information. Attackers frequently change the victim’s IDs and passwords to lock the victim out of their information and devices.
Data breaches
A data breach occurs when an attacker gains unauthorized access to a person’s or organization’s information. Most data breaches target personal information and data of value, such as financial transactions, customer databases, user credentials, and email addresses. The Identity Theft Resource Center reports that through the third quarter of 2021, the number of publicly reported data events for the year reached 1,291, which surpasses the 1,108 data events recorded in all of 2020.
Resources on cyber terrorism techniques, motives, and perpetrators
- U.S. Department of Homeland Security, “Strategic Framework for Countering Terrorism and Targeted Violence” — This report describes the DHS Cybersecurity and Infrastructure Security Agency that works with states to shore up vulnerabilities in public communication and transportation networks.
- Cisco, “What Is a Cyberattack?” — Among the topics discussed in the article are botnets, SQL injection, zero-day exploits, and DNS tunneling.
Effects of cyber terrorism on businesses and individuals
The impact of cyber terrorism attacks on companies and individuals includes the cost of protecting against increasingly sophisticated attacks. As ransomware becomes more prevalent, companies and individuals are more exposed to the expense of paying ransomware demands and recovering data lost as the result of a ransomware attack.
The World Economic Forum identifies the five greatest cybersecurity challenges facing organizations, governments, and people as cyberattacks increase in number and sophistication:
- Society’s growing dependence on technology makes everyone more vulnerable to attacks on government services, healthcare systems, transportation networks, and communication systems. Solutions become more difficult as national boundaries dissipate and distinctions blur between physical and digital realms.
- Inconsistent and outdated regulations complicate enforcement and help criminals avoid prosecution.
- The growing interdependence of industrial and financial systems makes organizations and individuals more dependent on third parties whose accountability is uncertain.
- The level of expertise in the data security industry can’t keep pace with advances and innovations of cybercriminals. This leaves organizations and individuals reacting to cyberattacks rather than preventing them.
- The likelihood that a cybercriminal will be caught and convicted is estimated to be as low as 0.05% in the U.S., according to figures compiled by Third Way. Cybercrime enforcement needs to be addressed internationally.
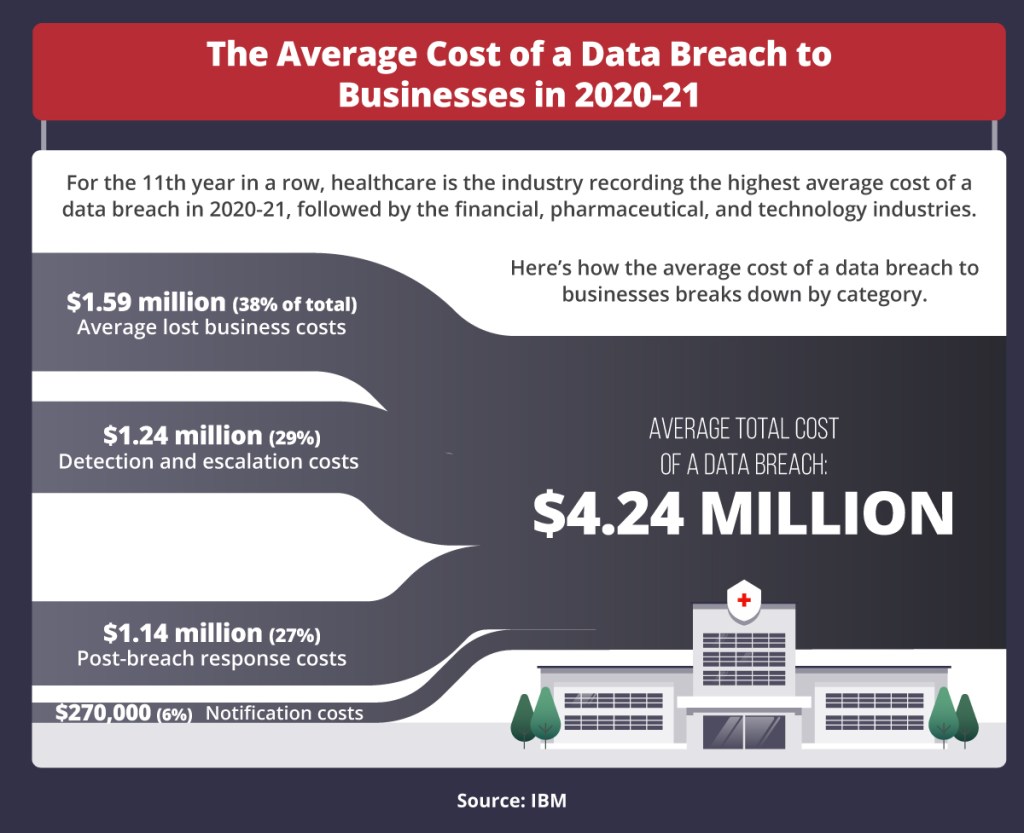
Statistics on cyber terrorism attacks and computer security costs
Cybercrime costs organizations an estimated $1.8 million each minute, according to security vendor RiskIQ’s 2021 Evil Internet Minute report. Here are other statistics on the prevalence of cyberattacks and the costs of securing systems from attacks:
- The average cost to an organization of a single breached data file was $161 between May 2020 and March 2021 (up from $146 in the previous annual timeframe), according to IBM’s Cost of a Data Breach Report 2021.
- The average total cost of a data breach to an organization in the U.S. was $9.05 million between May 2020 and March 2021; the global average cost per organization was $4.24 million.
- These are the most common types of data compromised in a breach, according to IBM:
- Customer personally identifiable information (PII): involved in 44% of all breaches
- Anonymized customer data: 28%
- Intellectual property: 27%
- Employee PII: 26%
- Other sensitive data: 12%
- The average amount of time required for an organization to identify and contain a data breach was 287 days during the May 2020 and March 2021 timeframe (up from 280 days the previous year).
- Gartner estimates that companies will spend more than $150 billion on computer security in 2021, which is 12% more than the $134 billion they spent in 2020.
- McAfee reports that the noncash damage done by a cyberattack includes opportunity costs of resources that are idled by the attack, and the added system downtime, which represents a cost to organizations that averages $590,000.
- DDOS attacks increased by 11% in the first half of 2021 from the first half of 2020, reaching a total of 5.4 million.
Resources on the impact of cyber terrorism
- Government Technology, “Data Breach Numbers, Costs and Impacts All Rise in 2021” — Topics include whether a ransomware attack is a data breach, and the costs of data breaches to U.S. organizations and overseas firms.
- CNN, “Hackers Have a Devastating New Target” — The implications of increasing cyber terrorism attacks on physical infrastructure in the U.S. are discussed here.
Cyber terrorism prevention tips
The rise in remote work as a result of COVID-19 precautions has increased the risks of cyber attacks for businesses and their employees. Organizations are responding by implementing cybersecurity best practices designed specifically to protect computer networks, digital devices, and the data they contain in dynamic work environments.
Cybersecurity best practices
Preventing cyber terrorism attacks and minimizing the damage of attempts to breach an organization’s systems begin with employee education. In addition to learning how to spot phishing attempts and other potential sources of malware, workers can adapt their daily processes to reduce the chances of a successful attack.
- Minimize data transfers: Avoid replicating data on too many systems, especially mobile devices. Doing so limits the potential damage should an individual system or device become compromised.
- Verify download sources: Restrict the sites you download software and files from, and scan files for viruses before downloading (most browsers and other software perform a virus scan automatically, but the programs aren’t foolproof).
- Keep software and systems patched and updated: The one action that will prevent the greatest number of potential malware threats is ensuring that software is set to update automatically. When prompted that an update is available for operating systems or other critical software, download and install the update as soon as possible.
- Use end-to-end encryption and two-factor authentication: Set browsers and other software to encrypt all communications automatically. Using a virtual private network (VPN) service adds a level of protection for extremely sensitive data transfers. Two-factor authentication requires that a cyberattacker gain access to two of your devices, such as your computer and smartphone, for a successful attack.
The steps that organizations need to take to prevent cyberattacks focus on two areas:
- Choose effective data breach monitoring tools: Enterprises use an average of 29 separate security monitoring tools, according to a report from Trend Micro, yet many are unused or underused because they can’t be integrated, companies lack employees with the expertise to use them, they’re out of date, or the firms simply don’t trust them.
- Devise an attack response plan: The plan is intended to ensure that the organization can continue to function in the aftermath of an attack. The plan can also reduce system downtime by delegating responsibilities clearly to avoid gaps and delays in plan implementation.
Resources on cyber terrorism prevention and mitigation
- PurpleSec, “How to Prevent the Top Cyber Attacks in 2021” — This article contains information on performing vulnerability assessments, conducting penetration testing, securing information and event management (SIEM), and using intrusion detection and prevention software.
- Reuters, “Ransomware State of the Union: Regulations, Trends and Mitigation Strategies” — Topics include the Office of Foreign Assets Control’s recent advisory on ransomware payments and reports on cybersecurity published by the Securities and Exchange Commission and the Financial Industry Regulatory Authority.
Joining forces to combat the growing cyber terrorism threat
Combating cyber terrorism begins by ensuring that governments, businesses, and individuals are aware of the growing threat of cyberattacks and know how to thwart such attacks. Computer security professionals play a central role in preventing and mitigating the threats posed by cyber terrorists to government agencies, organizations, and communities. A combination of user education and next-generation security techniques will keep cyber terrorists and other online criminals at bay.
Infographic Sources
IBM, “Cost of a Data Breach Report 2021”
U.S. Federal Bureau of Investigation, “Cyber Crimes Most Wanted”

