Cyber Crime Investigation: Making a Safer Internet Space
Tables of Contents
- What Is a Cyber Crime?
- Types of Cyber Crime
- What Is a Cyber Crime Investigation?
- How to Prevent Cyber Crime
- Fighting Cyber Crime Is Everyone’s Responsibility
In July 2021, hackers targeted Kaseya, a U.S. information technology firm, in a ransomware attack that affected up to 1,500 businesses worldwide, from the U.S. to Sweden to New Zealand. The hackers demanded $70 million to restore the impacted services. Nearly every type of organization — from public schools and health services systems to oil pipelines and beef processing plants — has fallen victim to this type of attack in 2021.
Criminal activity taking place in the digital world, known as cyber crime, comes in various forms. Like in the physical world, cyber crime is investigated by trained professionals who gather and secure evidence to confront cyber criminal activity and prosecute crimes. This type of investigation is known as a cyber crime investigation.
According to Cybercrime Magazine, the projected cost of cyber crime to the global economy will be $10.5 trillion annually by 2025. Cyber criminal activity can also put lives at risk. Earlier this year, hackers threatened the water supply of a small town, raising concerns about the impact cyber criminals can have on the health and safety of entire populations. These threats highlight the importance of cyber crime investigations and their role in making the internet a safer place for society and business.
What Is a Cyber Crime?
For most any crime that takes place in the physical world, a digital version of that crime exists in the cyber world. For example, a kidnapper may hold a hostage until their financial requests are met. In the digital realm, a type of cyber crime known as computer hacking (including ransomware) involves a hacker breaking into a computer system and holding an organization’s data hostage until a ransom is paid.
So, exactly what is cyber crime, and how does it differ from traditional criminal activity? There are three main differentiators:
- Digital technology such as computers, mobile devices, and networks are the primary tools used to commit cyber crimes.
- Cyber crime is not physical and involves targeting information about individuals, corporations, or governments for ill intent.
- Cyber crime has no geographic limitations — cyber criminals can reside thousands of miles away from their intended targets.
Types of Cyber Crime
As mentioned above, crimes typically associated with the physical world, such as committing fraud or stealing intellectual property, have online versions as well. That transition is enabled by computers and digital tools and technologies. Below are examples of different types of cyber crime:
Computer Hacking
The term “computer hacking” is often used as a catchall phrase to describe cyber crime. By definition, computer hacking means the modification of computer software and hardware to gain access to data such as passwords or introduce malware to computer systems and networks.
Ransomware, a type of cyber extortion, is a type of computer hack. So is phishing. In a phishing attempt, an email looks like it comes from a person or organization the user knows, but it’s really an “e-scam.” The email message may look genuine and tricks the user into clicking on a link or downloading an attachment that compromises the computer with malware, such as a virus.
Copyright Infringement
Copyright infringement is a type of cyber crime that involves theft of intellectual property, which can range from technology, movies, and music to inventions, ideas, and creative expressions such as art. The proliferation of digital technologies that facilitate file sharing through internet networks has made this type of cyber crime a growing threat to individuals and businesses. The consequences of copyright infringement are typically monetary.
For example, a startup technology company can lose its advantage if a competitor steals its code. In conducting cyber crime investigations in this area, the FBI collaborates with copyright and trademark owners, as well as online marketplaces and payment service providers that may inadvertently facilitate this type of cyber crime.
Cyber Stalking
With the rise of social media, people can easily share life experiences, interests, restaurants they’ve visited, and even vacation pictures. However, this sharing may gain the attention of cyber stalkers. NordVPN reports that more than 40% of adults have experienced some type of online harassment or cyber stalking, with women being the most targeted.
It is important to distinguish cyber stalking from researching a person’s background on the internet. For example, an employer may want to learn a little more about a newly hired employee, so they may take a glance at the individual’s Instagram account. This is not cyber stalking, as it is not intended to result in a nefarious act. On the other hand, cyber stalkers surveil their victims to harass, embarrass, or threaten them.
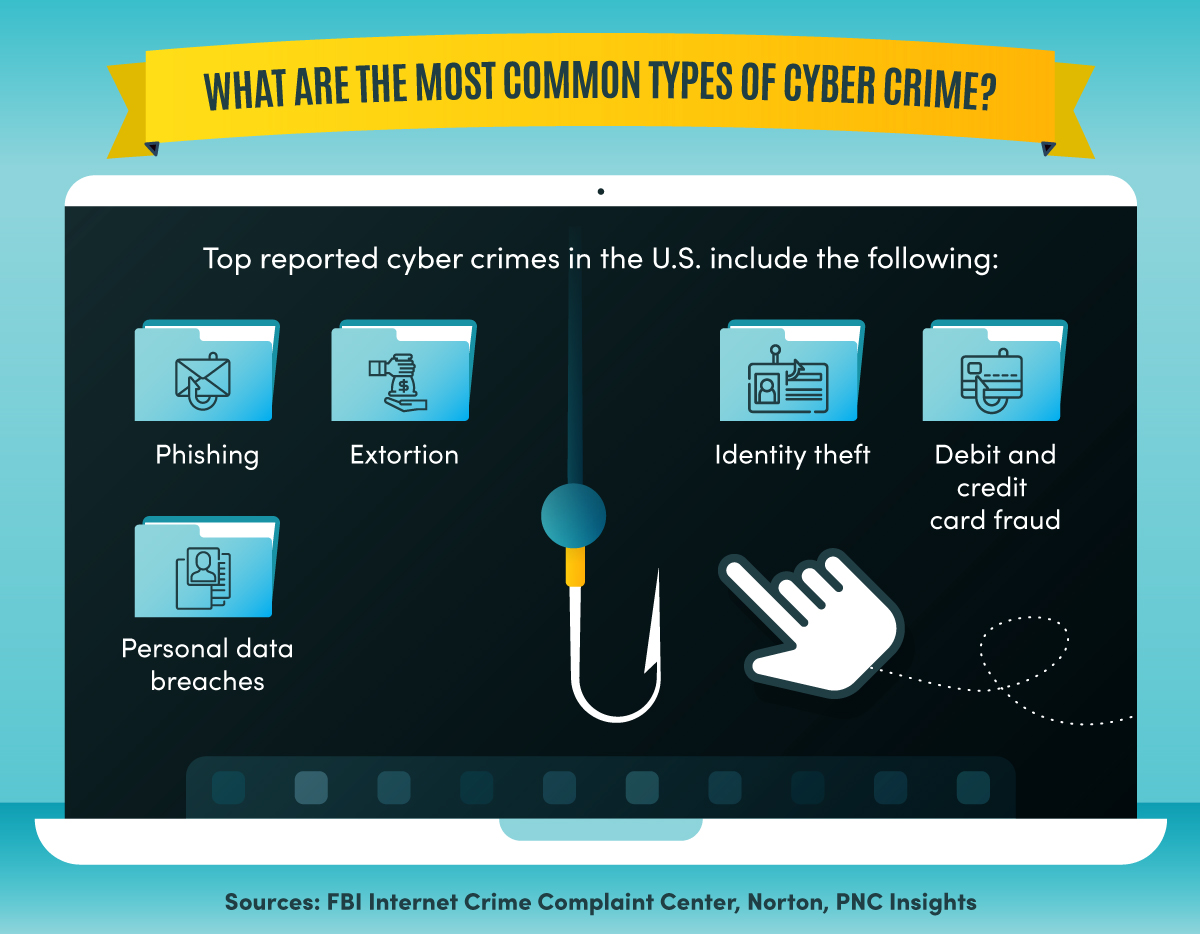
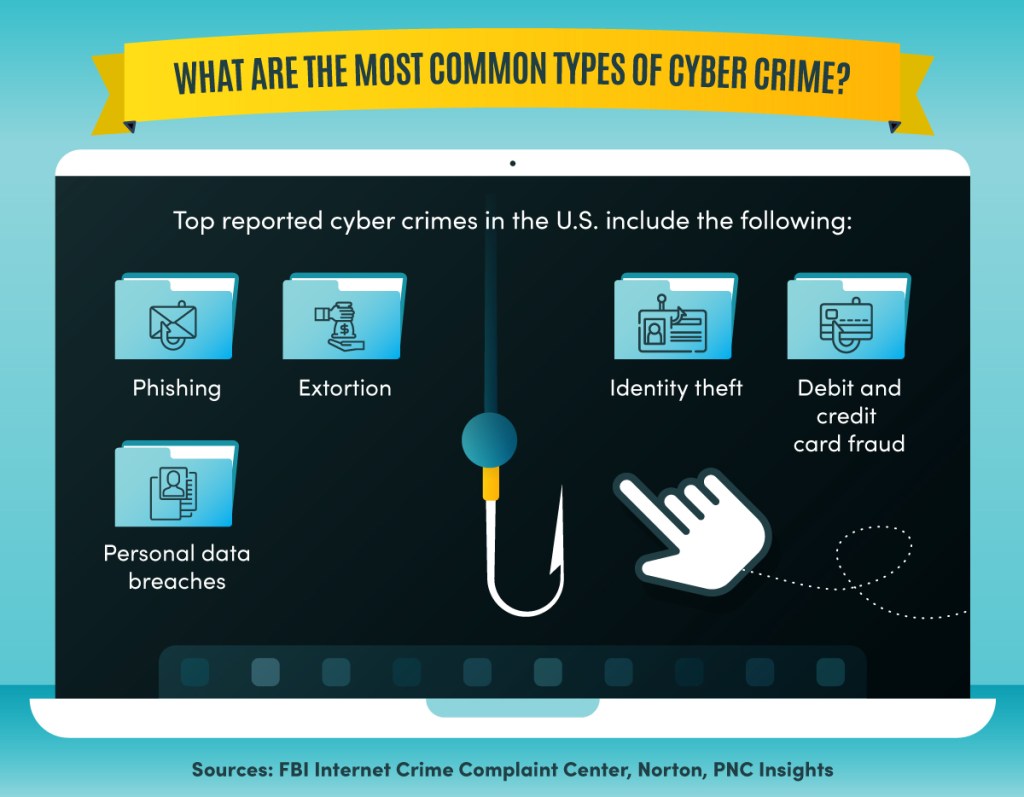
Top reported cyber crimes in the U.S. include phishing, extortion, identity theft, debit and credit card fraud, and personal data breaches.
DDoS Attacks
Picture for a moment thousands of vehicles headed on the same highway in one direction — a traffic jam seemingly going nowhere. That’s how a DDoS (distributed denial-of-service) attack works, except that instead of cars and trucks, data is bottlenecked. Another difference is that a DDoS attack is a malicious attempt to disrupt normal data traffic in the digital world.
A DDoS attack works by implementing malware that allows a hacker to target a network server and overwhelm it with an overflow of internet traffic. It affects the surrounding infrastructure of a server as well, causing systems and machines to crash. In a cyber crime investigation, a sudden surge of data patterns or suspicious amounts of traffic coming from a single IP address — a unique numerical identifier for a device on a computer network — can help point to the origin of a DDoS attack.
Extortion
Extortion comes in various forms. One way a cyber criminal extorts online is through ransomware. Another form of extortion that has made the headlines is “cryptojacking.” Organizations and individuals who fall victim to a successful cryptojack attack are placed in an unfavorable position and then forced to pay a hacker large sums of money using cryptocurrency such as bitcoins. Cryptojackers take advantage of the decentralized nature of cryptocurrency to operate anonymously and in the shadows. However, in the recent hack of the Colonial Pipeline in the U.S., the U.S. Justice Department was able to recover $2.3 million paid in bitcoins to hackers.
Fraud
Fraud is described as a deceptive practice to gain an unfair advantage or for personal enrichment. For example, a company may include fictitious payments, invoices, or revenues to present a false picture of its financial state to acquire investment or tax advantages. In the digital world, credit and debit card fraud is a growing problem.
Fraud can take place in the physical world and be extended into the digital realm. For example, a fraudster can use a skimming device to steal information from individuals who are using their credit or debit card at a credit card processing device or ATM. A hacker can also use malware to acquire customer credit card information from card processing software. The information obtained about a consumer can then be sold online or used to make purchases.
Identity Theft
Identity theft is an invasive online crime that can have long-term damaging effects on a person’s finances, reputation, and more. For example, using your personal information, an identity thief can open new credit card accounts in your name without your knowledge. According to the Federal Trade Commission, signs of having been the victim of identity theft include inexplicable checking account withdrawals, getting refused by merchants, receiving debt collection calls for debts that are not yours, and seeing charges on your credit report that you never authorized.
Online Predators
Online predators find targets, typically young children and adolescents, on popular social media sites. They often pretend to be the same or a similar age as their target and, using fake profiles, earn the trust of the most vulnerable. Through this act of grooming, they may pressure a child to send explicit images of themselves or share information about themselves, which can lead to a kidnapping, violent attacks, and sexual exploitation.
The FBI reports that every year there are thousands of cases involving crimes against children, and this includes online predators. According to the National Center for Missing and Exploited Children, its tip line received over 21.7 million reports regarding exploited children in 2020.
Personal Data Breach
A personal data breach describes when a hacker breaks into a computer system to steal records and data about individuals, such as user passwords, credit card information, and even health records. This type of cyber crime is most common in the business world. The biggest data breaches in history have affected the accounts of millions, and even billions, of users. An example includes the attack on Yahoo over three years which resulted in 3 billion accounts being breached. According to Norton, a data breach can occur in four ways: through system vulnerabilities, such as out-of-date software; weak passwords; drive-by downloads, which occur when a user visits a compromised website; and targeted malware attacks.
Prohibited/Illegal Content
This type of cyber crime often coincides with online predator activity, which may involve individuals preying on children online to try to obtain sexually explicit images. But prohibited/illegal content on the internet also includes footage of criminal activity and real or simulated violence. Content that promotes illegal activity, such as making weapons or bombs and extreme political or hateful views that can radicalize vulnerable people to perform criminal acts, is also considered illegal content. In business, prohibited content can include content on streaming services that was accessed without authorization and IP addresses that were acquired to commit fraudulent activities.
What Is a Cyber Crime Investigation?
A comparison of cyber crime investigations and physical-world criminal investigations reveals a primary difference: evidence in criminal investigations is mostly digital in nature.
A cyber crime investigation is the process of investigating, analyzing, and recovering forensic data for digital evidence of a crime. Examples of evidence in a cyber crime investigation include a computer, cellphone, automobile navigation system, video game console, or other networked device found at the scene of a crime. This evidence helps cyber crime investigators determine the perpetrators of a cyber crime and their intent.
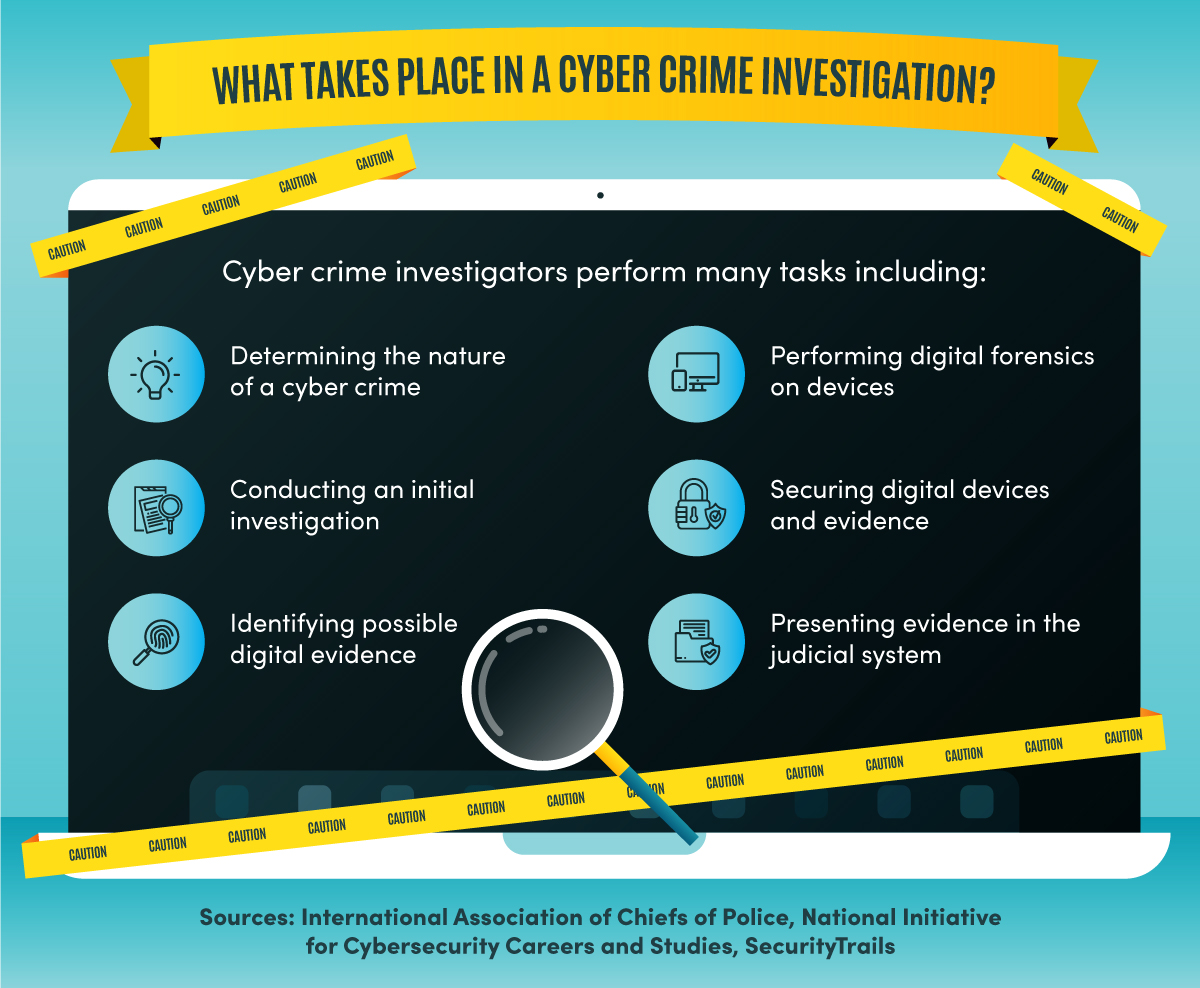
Cyber crime investigators perform many tasks, including determining the nature of a cyber crime, conducting an initial investigation, identifying possible digital evidence, performing digital forensics on devices, securing digital devices and evidence, and presenting evidence in the judicial system.
Organizations That Conduct Cyber Crime Investigations
The following organizations aim to prevent cyber crime from happening through deterrence, monitoring, and education:
Criminal Justice and Law Enforcement Agencies
The criminal justice system is made up of a network of agencies, including law enforcement, the judiciary, and corrections. Individuals who work in criminal justice agencies include law enforcement officers, prosecutors, and judges. These agencies work independently, yet work together to investigate and prosecute violations of cyber crime laws. Each branch of the criminal justice system is responsible for a certain area of the criminal justice process.
- Law enforcement (police officers, agents, and investigators) is responsible for gathering evidence of a crime, arresting a suspect, and charging the suspect with the crime.
- The judiciary consists of lawyers who present their evidence against the charged individual, lawyers who defend the individual, judges who preside over the proceedings, and juries who decide whether the individual is guilty or innocent.
- Corrections agencies ensure that prosecuted criminals remain behind bars during their sentences.
The FBI is the primary federal law enforcement agency that investigates cyber crime domestically and abroad. Other agencies include the U.S Secret Service, U.S. Immigration and Customs Enforcement (ICE), U.S. Postal Inspection Service, and the Bureau of Alcohol, Tobacco, Firearms and Explosives (ATF). These agencies have local offices in each state. State and local law enforcement agencies also investigate cyber crimes that take place in their jurisdictions.
Private Security Firms
The private sector remains one of the most vulnerable to internal and external threats. Many of the largest companies have their own cybersecurity departments to monitor, prevent, and mitigate cyber attacks. Some private sector companies hire specialized cybersecurity firms to help them defend against cyber attacks. With the creation of the Cybersecurity and Infrastructure Security Agency (CISA) in 2018, the private sector can leverage government resources to address cybersecurity problems.
Cyber Crime Investigation Techniques
Activities that a computer crime investigator performs include recovering file systems of hacked computers, acquiring data that can be used as evidence to prosecute crimes, writing reports for use in legal proceedings, and testifying in court hearings. Cyber crime investigation techniques include:
- Performing background checks: Establishing the when, where, and who of a crime sets the stage for an investigation. This technique uses public and private records and databases to find out the backgrounds of individuals potentially involved in a crime.
- Gathering information: This technique is one of the most critical in cyber crime investigations. Here, investigators ask questions such as: What evidence can be found? What level of access to sources do we have to gather the evidence? The answers to these and other questions provide the foundation for a successful investigation.
- Running digital forensics: Cyber crime investigators use their digital and technology skills to conduct forensics, which involves the use of technology and scientific methods to collect, preserve, and analyze evidence throughout an investigation. Forensic data can be used to support evidence or confirm a suspect’s involvement in a crime.
- Tracking the authors of a cyber crime: With information about a crime in hand, cyber crime investigators work with internet service providers and telecommunications and network companies to see which websites and protocols were used in the crime. This technique is also useful for monitoring future activities through digital surveillance. Investigators must seek permission to conduct these types of activities through court orders.
Cyber Crime Investigation Resources
The following organizations and agencies offer additional resources about cyber crime and cyber crime investigations.
- Insurance Information Institute, “Facts + Statistics: Identity Theft and Cybercrime”: To help individuals understand the scope of cyber crime, this resource provides a wide range of statistics and data.
- International Association of Chiefs of Police, Cyber Crime Community Resources: This page links to various other resources to increase the understanding of cyber threats.
- FBI Internet Crime Complaint Center IC3: This resource from the FBI has been set up to help individuals file a complaint or report an internet crime.
- SecurityTrails, “Cyber Crime Investigation: Tools and Techniques Explained”: This resource introduces how public and private agencies deal with cyber crimes using various tools and techniques.
- S. Federal Bureau of Investigations, What We Investigate: This resource explains the types of cyber crime the FBI investigates and provides examples of common cyber crimes.
- United States Secret Service, Preparing for a Cyber Incident: This resource provides guidance on how organizations can prepare for cyber events before they happen and how to respond during and after an incident.
How to Prevent Cyber Crime
How can individuals and organizations help protect themselves from cyber crimes? The following are examples of how to prevent cyber crime, including tactics, steps, and strategies:
Follow Cybersecurity Best Practices and Guidelines
Employers typically establish cybersecurity policies or regulations based on best practices to protect their employees and critical business data. These policies can be adopted for personal use as well. Commonsense practices include backing up data and not sharing personal information such as Social Security numbers when responding to unsolicited emails. Additional practices include avoiding pop-ups and unknown email attachments and using strong passwords.
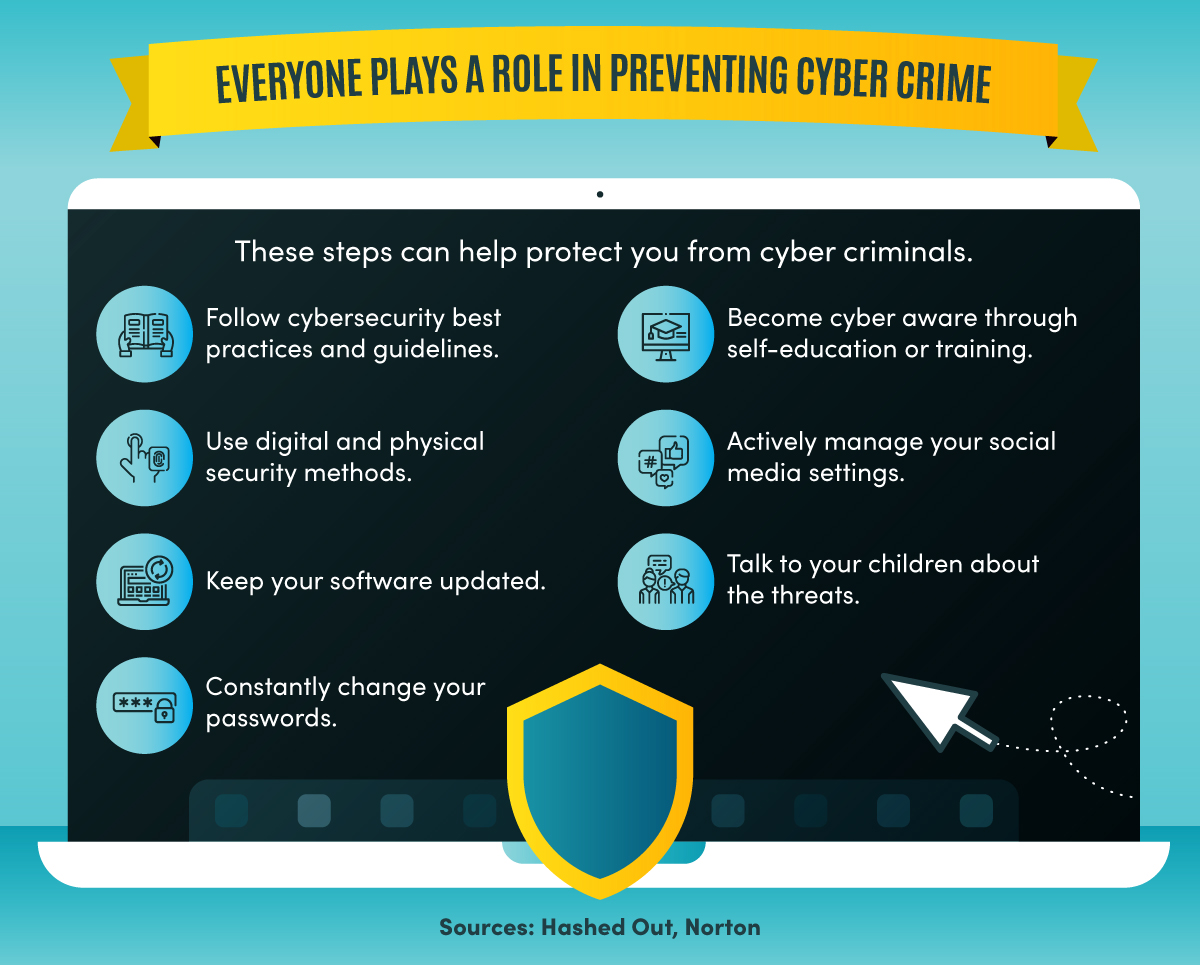
These steps can help protect you from cyber criminals: follow cybersecurity best practices and guidelines; use digital and physical security methods; keep your software updated; constantly change your passwords; become cyber aware through self-education or training; actively manage your social media settings; and talk to your children about the threats.
Use Digital and Physical Security Methods
Firewalls and antivirus software are a first line of defense to protect your devices from cyber attacks. For example, a firewall is a technical tool that helps to prevent unauthorized access to unsecure websites. Antivirus software can detect viruses and defend your device from getting infected. Additionally, a commonsense strategy is to never leave a laptop unattended in a public place.
Update Software Regularly
Software developers periodically send automated software update messages. For example, Microsoft update messages can appear when starting up your laptop. These updates fix bugs and improve performance, and they enable individuals to manage security risks and keep their systems protected. These updates are vital to maintaining the latest version of software, which also includes patches to resolve previously identified vulnerabilities.
Become Cyber Aware
A key step to prevent a cyber attack from affecting your device is to educate yourself. Cyber criminals often attack the edge of the network — that is, where end users are. For example, to gain access to a corporate database, a cyber criminal may execute a phishing attempt on a single user. If that user clicks on the link in the phishing email, the cyber criminal may be able to gain access to the company’s entire network. Therefore, organizations need to train their employees on how to identify threats.
Manage Your Social Media Settings
According to the Pew Research Center, YouTube is the most used social media site in the U.S. — 81% of Americans use it. When it comes to social media use, Facebook comes a close second at 69%. For younger adults, platforms like Instagram and WhatsApp are more popular. The common thread with all social media platforms is that anyone in the world can see users’ activities — what they posted and what they liked, for example. Though social media platforms allow users to control who sees the information they share, the steps in implementing these security settings vary by site. By reviewing and adjusting the privacy settings in the platforms they use, users can protect themselves.
Talk to Your Children About the Threats
Common Sense Media reports that 84% of teenagers and about 53% of children own a smartphone. Children have access to a wide range of digital media, from TikTok videos to online learning platforms. Parents need to discuss the potential dangers of online threats with their children to help keep them safe. This requires listening while being straightforward about the types of content and contacts that are inappropriate.
Cyber Crime Prevention Resources
The following websites offer recommendations and tips for preventing cyber crime:
- DeltaNet International, “Why Is It Important to Manage Your Privacy Settings on Social Media?”: This resource explains why managing privacy settings is important to mitigate dangers when using social media.
- Federal Trade Commission, Talk to Your Kids: This resource provides parents with tips on how to discuss privacy, identity, and online security topics with their children.
- Norton, “10 Cybersecurity Best Practices That Every Employee Should Know”: This resource provides top cybersecurity best practices for employers.
Fighting Cyber Crime Is Everyone’s Responsibility
Although technology is a useful tool for fighting cyber crime, people must understand that cyber crime is a human problem. Countering cyber crime requires a simple approach. Each person who is willing to build awareness of the problem and take appropriate steps, as described in this article, helps reduce the impact of cyber criminal activity.
Recommended practices, such as changing passwords and never clicking on a suspicious email, and commonsense activities, such as never leaving your laptop or device unattended, not only help you protect yourself, but they also take away potential targets from cyber criminals. Cybersecurity professionals need all the help they can get in terms of gathering information about potential crimes. By reporting cyber crimes to the proper authorities, you are playing a key role in addressing cyber threats.
Infographic Sources
FBI Internet Crime Complaint Center, “Internet Crime Report 2020”
HashedOut, “How to Prevent Cybercrime: 9 Helpful Tips”
International Association of Chiefs of Police, Digital Evidence
National Initiative For Cybersecurity Careers and Studies, Cyber Investigation
Norton, “11 Ways to Help Protect Yourself Against Cybercrime”
Norton, “Top 5 Cybercrimes in the U.S., from the Norton Cyber Security Insights Report”
PNC Insights, “Do You Know the Most Common Types of Cybercrime?”
SecurityTrails, “Cyber Crime Investigation: Tools and Techniques Explained”

