A Look at IOT Security and Potential IssuesA Look at IOT Security and Potential IssuesA Look at IOT Security and Potential Issues
The internet of things (IoT) refers to any device connected to the internet. The number of connected smart products has increased immensely over the years, resulting in serious challenges to privacy and security.
To learn more, check out the infographic below about online Cybersecurity.
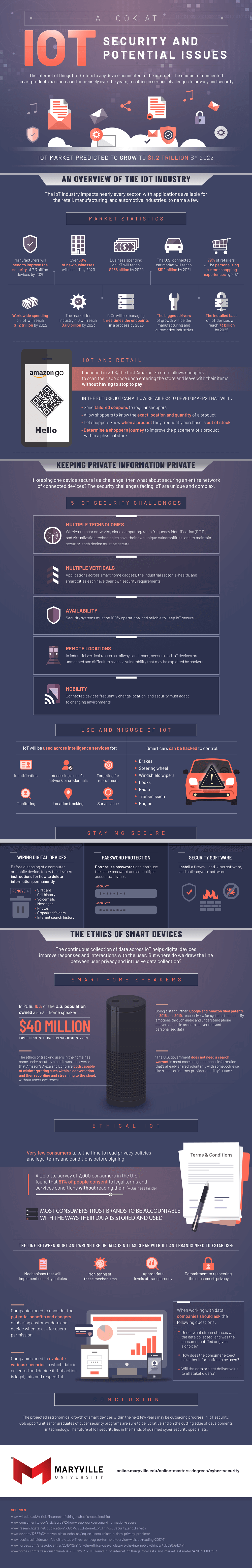
An Overview of the IoT Industry
The IoT industry impacts nearly every sector, with applications available for the retail, manufacturing, and automotive industries, to name a few.
Market Statistics
IoT is big business. Business spending on IoT is thought to reach $238 billion by 2022, and worldwide spending on IoT is predicted to reach $1.2 trillion by 2022. Some of this growth is driven by innovation. More than 60% of new businesses will use IoT by 2020, the U.S. connected car market is projected to reach $514 billion by 2021, and 78% of retailers are predicted to provide personalized in-store shopping experiences by 2021. From an industry perspective, the manufacturing and automotive industries are thought to be IoT’s biggest drivers.
IoT and Retail
One of the prime examples of IoT’s retail influence is Amazon Go. Launched in 2018, the first Amazon Go store allows shoppers to scan their app once entering the store and leave with their items without having to stop to pay. In the future, IoT can allow retails to develop apps that can potentially enhance a customer’s experience through things like tailored coupon delivery and up-to-date information on a product’s availability and in-store placement.
Keeping Private Information Private
If keeping one device secure is a challenge, then what about securing an entire network of connected devices? The security challenges facing IoT are unique and complex.
5 IoT Security Challenges
IoT growth also means IoT-related security is also on the upswing. This presents a quintet of key challenges that must be faced. The concept of multiple technologies creates potential issues, as tech like wireless sensor networks and cloud computing have their own unique vulnerabilities. Multiple verticals ranging from smart home gadgets to e-health devices also pose challenges because they have their own security requirements. Additionally, keeping security systems available and 100% operational is key to keeping data safe. Another issue involves keeping industrial vertical IoT devices in remote locations safe from hacker exploitation. Finally, keeping connected mobile devices secure is an important challenge to meet.
Use and Misuse of IoT
IoT concepts can be used for good. For example, IoT will be used across intelligence services for key concepts like identification, location tracking, monitoring, and surveillance.
Unfortunately, a downside of IoT abuse also lurks. A dramatic example of this relates to smart cars. Without proper security, smart cars can be hacked to control the brakes, steering wheel, engine, and more.
Staying Secure
One of the proactive ways to maintain security involves wiping digital devices. Before disposing of a computer or a mobile device, it’s advisable to remove things like SIM cards, call history, messages, photos, and internet search history. Password protection is another key method of keeping things secure. Individuals should not reuse passwords and shouldn’t use the same password across multiple accounts and devices. Finally, installing security software like firewalls, antivirus software, and anti-spyware software can be vital for security purposes.
The Ethics of Smart Devices
The continuous collection of data across IoT helps digital devices improve responses and interactions with the user. But where do we draw the line between user privacy and intrusive data collection?
Smart Home Speakers
In 2018, 10% of the U.S. population owned a smart home speaker. Projections indicate that the expected sales of these devices were to hit $40 million in 2019. Google and Amazon acted on this projection by filing patents that sought to identify emotions through audio and understand phone conversations to deliver relevant, personal data.
At the same time, the ethics of tracking users in the home has come under scrutiny since it was discovered that Amazon’s Alexa and Echo are both capable of misinterpreting cues in a conversation and then recording and streaming to the cloud without users’ awareness. This could create issues: according to Quartz, “The U.S. government does not need a search warrant in most cases to get personal information that’s already shared voluntarily with somebody else, like a bank or internet provider or utility.”
Ethical IoT
Very few consumers take the time to read privacy policies and legal terms and conditions before signing. A Deloitte survey of 2,000 American consumers revealed that 91% of people consent to legal terms and service conditions without reading them. This can be tricky when it comes to IoT, as most consumers trust brands to be accountable with the ways their data is stored and used.
The line between right and wrong use of data is not as clear with IoT. As such, brands need to establish monitored mechanisms that will implement security policies, complete with appropriate levels of transparency and a commitment to respecting the consumer’s privacy.
Companies also need to consider the potential benefits and dangers of sharing customer data and decide when to ask for users’ permission. Additionally, they need to evaluate various scenarios in which data is collected and decide if that action is legal, fair, and respectful. When working with data, companies should always ask what circumstances surround data collection, consumer expectations in terms of usage, and the level of value it delivers to stakeholders.
Conclusion
The projected astronomical growth of smart devices within the next few years may be outpacing progress in IoT security. Job opportunities for cybersecurity program graduates are sure to be lucrative and on the cutting edge of technological developments. The future of IoT security lies in the hands of qualified cybersecurity specialists.
Be Brave
Bring us your ambition and we’ll guide you along a personalized path to a quality education that’s designed to change your life.

