Types of Hackers: The Hats They Wear and What They Do
Tables of Contents
The technology that we rely on to navigate our everyday lives can make us an appealing target for skilled computer experts, also known as hackers, with malicious intent. Novel ways to take advantage of flaws in networks and computer systems are discovered every day. According to a report from the cybersecurity firm Forescout Technologies, in December 2020, millions of household and business smart devices — including devices that power critical infrastructure — were ripe for the taking by an intrepid hacker with the desire for mayhem.
But hackers aren’t all looking to break into government computer systems or turn your smartphone into a spambot. Despite the stigma associated with hacking, many hackers work for corporations and government agencies. A bounty of career opportunities are available in the cybersecurity field for technophiles interested in deploying their hacking skills legitimately.
How can you tell if a hacker is nefarious or legit? Read on to discover the main types of hackers and how to distinguish them.
Understanding the different types of hackers
A hacker is a person who uses their extensive knowledge of computers and technology to solve a problem by means that may or may not require the illegal nullification of network security measures. Hackers are typically versed in multiple programming languages and networking protocols, along with computer system and network architecture.
The way to tell hackers apart is to look at the color of their metaphorical hats.
A shorthand:
- Black hats act with malicious intent.
- White hats are beneficent.
- Grey hats use black hat techniques but possess white hat intentions.
Both white and grey hat hackers have employment prospects in industry or government, but black hats are typically stuck evading the law. What differentiates each of them isn’t their techniques, which may look the same, but their intentions and ethical orientation.
Though many hackers are mainstream today, the origins of hacking lie in the do-it-yourself, anti-establishment counterculture of the 1960s.
A brief history of hacking
The first hackers were members of the Massachusetts Institute of Technology’s circa 1961 who hacked their electronic model trains to modify their functionality. They later switched to computers, tinkering with early IBM machines, and the modern hacker was born.
Late 1960s to early 1980s
With the 1969 advent of the Advanced Research Projects Agency Network (the transcontinental Defense Department network, commonly known as ARPANET), hackers became connected. Not only were the isolated university and government networks where they tested their mettle now interlinked, but diverse groups of hackers began to interact and form a recognizable subculture. Today, ARPANET forms the backbone of the internet.
Through the 1970s, computing technology improved exponentially. As technology advanced, hacking techniques evolved along with it. Phone hackers, aka “phreakers,” began to exploit telecommunications systems, taking advantage of the recent turnover of switching networks to electronic control. Steve Jobs and Steve Wozniak, the founders of Apple Computer, began their careers as phreakers.
The introduction of the personal computer in the 1980s precipitated even more interest in hacking techniques. With a PC in the home, being associated with a university or government lab was no longer required to access a network. At the same time, cybercrime began to rise. Piracy, intrusion into restricted systems, and distribution of malware proliferated.
Late 1980s to present day
In 1986 the U.S. Congress passed the Computer Fraud and Abuse Act (CFAA) to specifically address the problem of malicious hacking. The legislation prevents users from accessing a computer system or network “without permission.” Hackers and electronic rights organizations have pushed back against the CFAA because of its ambiguous language, and the CFAA has been amended multiple times since its passage.
During the 1990s and 2000s, and into the 2010s, the internet expanded its reach further, becoming ubiquitous. This has expanded the domain of the hacker as many electronics, from refrigerators to automobiles, now connect to a network of some kind. The late 1990s introduction of computer worms able to infect thousands of PCs and distributed denial-of-service (DDoS) attacks harnessing the power of hundreds of thousands of zombified devices signaled an escalation of black hat hacking techniques.
Hacking in shades of black, white, and grey
The hat system for distinguishing different types of hackers is widely reported to derive from the hats worn by characters in American Western films. Many believe that characters with black hats were the villains and characters with white hats were the heroes. However, this doesn’t actually bear out in truth. In the films themselves, white hats were just as likely to belong to bad guys as good guys.
But in real life, white hat hackers are the good guys, dedicated to protecting systems from breach by bad actors. And black hat hackers are the robbers trying to break into the town bank. Grey hat hackers are difficult to pin down, as their methods can be controversial, though their motives are generally pure.
White hat hacking: The “good guys”
White hat hackers are typically employed as security professionals for corporations or governments. They only hack into systems with permission, and only with positive intent — to report on vulnerabilities so they can be fixed, for example.
Black hat hacking: The “bad guys”
Black hat hackers may break into any system, anywhere, with no consent. They operate outside the law and are usually seeking some kind of personal gain, whether financial or informational. These hackers may also use their skills to protect and enable criminals of other stripes.
Grey hat hacking: Somewhere in between
Though grey hat hackers may break the law via their unauthorized intrusion into computer systems, the difference lies in their reasoning. Grey hat hackers are acting with benevolent intentions, such as when a hacker informs the public of a vulnerability in a company’s systems that could potentially impact them. Of course, grey hat hackers can still be prosecuted for criminal activities no matter the intent behind them.
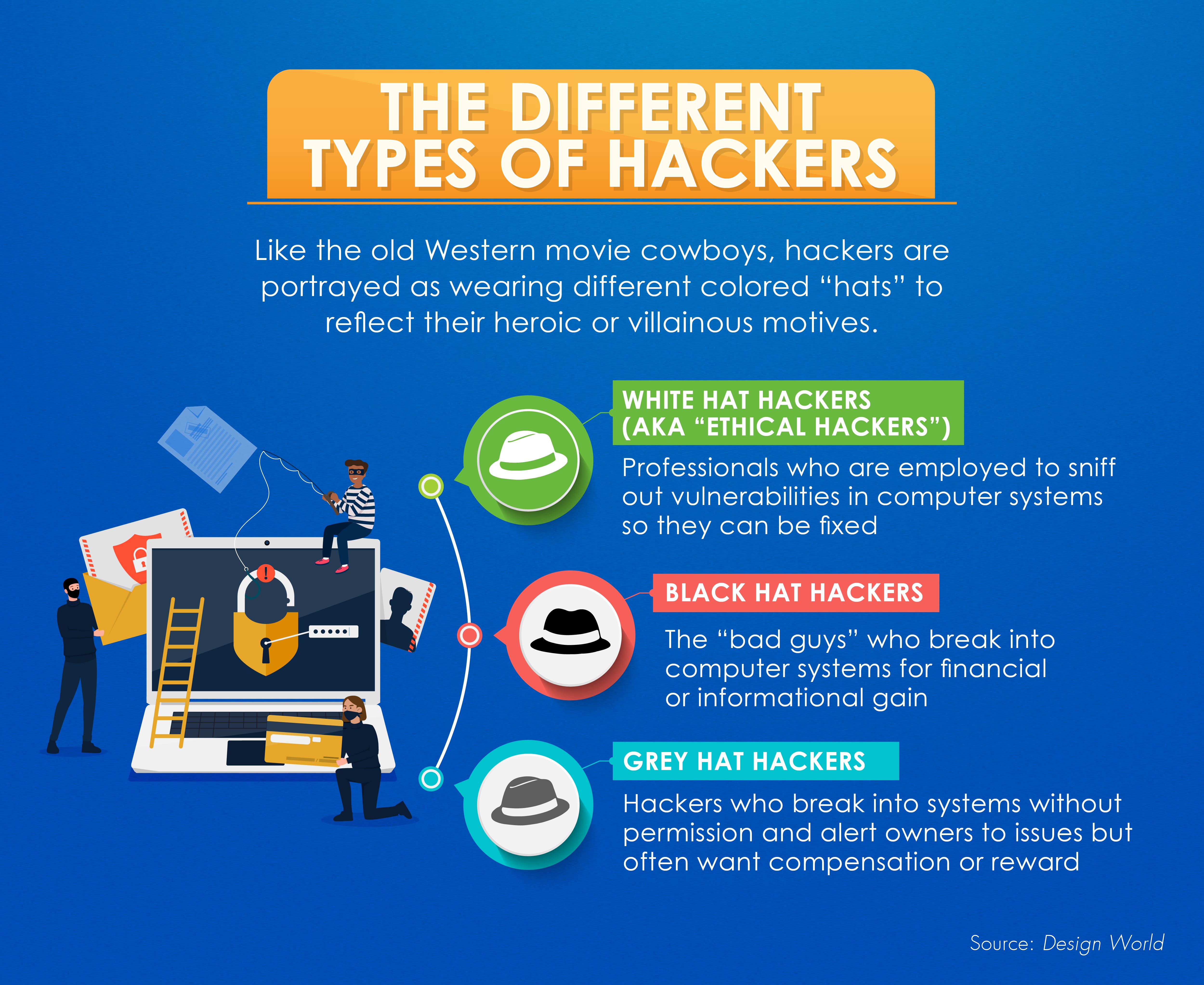
Like the old Western movie cowboys, hackers are portrayed as wearing different colored “hats” to reflect their heroic or villainous motives. White hat hackers (aka “ethical hackers”) are professionals who are employed to sniff out vulnerabilities in computer systems so they can be fixed. Black hat hackers are the “bad guys” who break into computer systems for financial or informational gain. Grey hat hackers break into systems without permission and alert owners to issues, but often want compensation or reward.
What is white hat hacking?
White hat hacking is often used interchangeably with ethical hacking. White hat hackers use hacking techniques at the behest of a client or employer to discover vulnerabilities in their networks and suggest ways to improve security. They may have a postsecondary degree in computer forensics or another specialty.
The key difference between white hat hackers and the rest of the pack is consent. White hat hackers work with permission.
What makes white hat hacking ethical?
Ethical or white hat hacking is done to improve security and prevent catastrophic breaches of information. Ethical hackers are often security professionals who adhere to a well-developed moral compass and understanding of the law.
Because of laws such as the CFAA, for hacking techniques like port scanning and penetration testing to be legal, a hacker must secure the authorization of the entity whose networks they intend to probe. If consent is not given and a hacker goes forward, they are treading outside of ethical hacking territory and into the land of the black and grey hats.
Where is white hat hacking used?
Nearly all industries benefit from the skills and expertise of security professionals, and white hat hackers possess a wide base of knowledge in computers and networking. White hat hackers are utilized by organizations from Uber to the Pentagon.
Some companies solicit individual hackers with cash for rooting out vulnerabilities, while others hire consulting firms to conduct security assessments and make recommendations. Most large corporations retain an information technology staff, so individuals versed in white hat hacking techniques may find themselves working in-house with other IT professionals as part of a security team.
Additional resources: Skills for white hat hacking
Every white hat hacker needs to have their basic skills down pat. These resources are a solid start.
- TCP/IP Network Administration, 3rd Edition, “Chapter 1: Overview of TCP/IP”. The first chapter of this classic network administrator’s guide is required reading for any hacker.
- Hacking Articles, “AlienVault: Threat Hunting/Network Analysis.” A hacker explains how they go about scanning networks for threats and securing against them.
- TutorialsPoint, Shell Scripting Tutorial. UNIX and Windows Server are the two platforms a hacker is most likely to encounter when interacting with networked computers. Both have robust shell scripting languages.
- WonderHowTo, “Database & SQL Basics Every Hacker Needs to Know.” Malicious hackers often use SQL injections to compromise the integrity of networked databases. Learning SQL programming is essential for a white hat hacker to defend their clients against these attacks.
Who uses black hat hacking?
Black hat hackers are the rule breakers of the hacking world. When a hack results in monetary damages or personal data leaks, these are usually the hackers behind it. However, the techniques these hackers use are often indistinguishable from those of white and grey hat hackers.
That means some white hat hackers by trade might engage in black hat hacking techniques in their free time because the term merely refers to any hacking into computer systems that is done without the permission of the system owner.
Black hat hackers: Villains or vigilantes?
Though nefarious motives are often ascribed to black hat hackers, they aren’t necessary. Whether or not they seek personal gain, the act of breaking into a system without consent is enough to place a hacker in the black hat category.
A black hat hacker may break into a system merely because it seems vulnerable, or alternately, because it presents a challenge. Some black hat hackers may have retained the countercultural attitude of hacking’s origins, viewing laws against network intrusion as an affront to the free expression of information.
Still others, such as the hacker collective Anonymous, may see themselves as cyber warriors who protect the people from exploitation by the state. Sites like WikiLeaks provide these self-styled vigilantes with a safe harbor for distributing the results of their exploits. Violating the law is incidental to such hackers, who believe unwaveringly in the right of the people to know what the government does in their name.
The age of cybercrime
Cybercrime is a multibillion-dollar drain on the world’s economy and can even present a threat to social stability.
In 1999, the Melissa virus shut down 1 million email accounts and slowed internet traffic to a near standstill in some regions. Just one year later, a hacker named mafiaboy executed the first documented DDoS attack, harnessing the combined computing power of several university networks to take down sites ranging from eBay to CNN.
Since 2010, individual cyberattacks by black hat hackers have escalated, and nations are now regularly engaging in digital warfare techniques. Social media platforms like Facebook and Twitter make it easy for black hats to use social engineering techniques to obtain sensitive information from unsuspecting users. Phreakers are diversifying, as well, with text-based phishing scams and robocall spoofing.
Recalling the events of the 2016 election, in December 2020, Russia was once again accused of involvement in a major breach of U.S. government and private sector computer systems. Cyber warfare between nations seems to have become a fact of modern life.

From worms and viruses to rootkits and keyloggers, malicious hackers have a variety of tools at their fingertips to gain access to and control over our data. These famous hacks show no one is immune. In 2008 the Conficker worm launched and goes on to infect millions of computers worldwide. In 2010 the Stuxnet worm was uncovered and infected 5,000 Iranian nuclear reactors. In 2014 home improvement giant Home Depot was hacked and 56 million customers’ financial information was exposed. In 2015 dating website Ashley Madison was hacked and 37 million users’ personal data was exposed. In 2016 the U.S. Democratic National Committee was hacked and documents were leaked. In 2020 the Twitter accounts of President Barack Obama, Elon Musk, and dozens more were commandeered for a Bitcoin scam.
Grey hat hacking: A blend of both worlds
The “grey” in grey hat hacking signifies the borderland these hackers inhabit. They straddle the line as far as legality and ethics. Grey hat hackers are not affiliated with any organization, though they may work in the technology industry by day. Though they operate outside the law, their intentions are generally good.
What makes grey hat hacking unique?
On the one hand, grey hat hackers often have noble motives. Grey hats tend to be off-duty white hats. Since one defining characteristic of all hackers is a desire to tinker with and test computer systems, sometimes a white hat strays into the grey territory without even realizing it.
On the other hand, what makes grey hat hacking different from white hat hacking is essentially the same thing that differentiates white hats from black hats: Grey hat hackers do not have permission to intrude on the systems they are hacking. Therefore, their actions are illegal.
The difference between grey hat hackers and black hat hackers, however, is this: Grey hats notify system administrators of their successful exploit so they can fix it, instead of making it public or leveraging their discovery for financial gain. Whether or not they are prosecuted for their actions ultimately depends on the attitude of the organization whose system they breached.
Grey hat hacking in industry
Some industries, like those in the technology sector, welcome the investigations of grey hat hackers and even encourage them. Once permission is granted, of course, a hacker moves back under the umbrella of white hat hacking. Also, many grey hat hackers still identify themselves as ethical hackers, since ethics are not necessarily tied to legality.
Choosing a career in ethical hacking
The employment opportunities for hackers who engage in ethical hacking practices are diverse. Their hands-on experience and affinity for challenge mean they are in demand to fill security roles. And many of the positions available to ethical hackers pay very well.
What jobs can an ethical hacker hold?
Information security is a broad field, and depending on the credentials a hacker holds, dozens of roles might be well-suited to their skills and experience. Some of the highest-paying positions in the field are:
- Forensic computer analyst: These professionals gather and analyze data related to cyberattacks and use advanced forensic techniques to investigate cybercrimes.
- Penetration tester: The classic ethical hacking career, penetration testers scan networks and computer systems for vulnerabilities.
- IT security architect: Security architects design, build, and maintain an organization’s digital security infrastructure.
- Chief information officer (CIO): An organization’s CIO is responsible for overseeing the operations of the entire IT department. This includes security professionals as well as those involved in day-to-day systems maintenance.
Who needs ethical hacking?
Since ethical hackers have a very diverse set of skills, virtually all industries can use their assistance. Openings for cybersecurity positions can be found in sectors from education to manufacturing.
However, industries that are vital to society are particularly interested in discovering and fixing network vulnerabilities before black hat hackers can take advantage of them. Financial institutions have begun to embrace ethical hacking after initially balking, likely due to an increase in costly breaches. Hackers also work with law enforcement to spy on criminals and combat cybercrime.
Companies whose primary business is conducted online also invest heavily in cybersecurity, as do technology companies that lean heavily on networked services for their daily operations.
Education for hackers
A bachelor’s degree in computer science or engineering is a strong foundation for an information security career. Earning an advanced degree such as a master’s in business or cybersecurity will improve an individual’s prospects for landing a senior position such as CIO.
Certifications are another path to obtain an ethical hacking education. Preparation for certification exams can be self-guided or instructor led. The CompTIA A+ certification is an industry standard that is required for many IT positions. Network+ and Cisco Certified Network Associate Routing and Switching (CCNA) certifications are also widely sought after by employers.
For hackers who would rather avoid the rigors of formal education, the certification path is a middle road, but to reach the heights of ethical hacking careers, some college may be required.
Additional resources: Careers in ethical hacking
- Forbes, “Building a Strong Foundation for a Career in Cybersecurity Penetration Testing.” Penetration testers evaluate networks’ intrusion protection. This article explains the knowledge and skills required to become a penetration tester and what employers look for in a candidate.
- Houston Chronicle, “What Does a Computer Security Specialist Do?” Computer security specialists, or information security analysts, protect the computer systems of businesses and organizations. Learn more about their day-to-day duties and responsibilities.
- The Balance Careers, “What Does a Chief Information Officer (CIO) Do?” For those who aspire to reach the top of the cybersecurity sector, The Balance offers a rundown of what to expect in a CIO position.
The future of hacking
As everything from microwaves to medical devices goes online, even our vital organs become vulnerable to hijack by malicious hackers. In our increasingly interconnected world, a large-scale cyberattack is an existential threat to nations and corporations alike. That means the future is bright for the good guys, the ethical hackers, whose services are likely to remain in high demand as organizations and governments scramble to secure their systems against new exploits.
Infographic Sources
Design World, “What Are the Three Types of Hackers?”
Forbes, “These 20 ‘Hackers’ Helped Shape the Cybersecurity Landscape Forever”
CSO, “John McAfee ranks the biggest hacks ever”
The New York Times, “Florida Teenager Is Charged as ‘Mastermind’ of Twitter Hack”

