Supply Chain Attack: Preventing Ransomware Attacks on the Supply Chain
Tables of Contents
In 2021, a turning point was reached in the battle against cybercriminals who target global supply chains with their ransomware attacks:
- Ransomware supply chain attacks became more ruthless: They attempted to cripple food networks, water supplies, and fuel distribution networks as well as hospitals and city governments, as the 2022 SonicWall Cyber Threat Report explains.
- The year saw an increase in the number of ransomware attacks and their severity: 623 million ransomware attacks were recorded worldwide in 2021, a 105% increase from the previous year. Security Intelligence reports that the average cost of remediating an attack more than doubled to $1.85 million from $761,106 in 2020.
- Manufacturers have replaced financial services firms as the principal targets of ransomware attackers: IBM reports that 23% of ransomware attacks in 2021 threatened manufacturing supply chains.
Ransomware supply chain attacks have the potential to inflict serious financial and reputational damage that can affect a company for years to come. Analysts predict an increase in “hub” attacks in 2022 and beyond as cybercriminals attempt to take advantage of companies that have extensive digital networks linking them with suppliers and customers.
The ransomware attack on information technology (IT) firm SolarWinds in 2020 now serves as a cautionary tale for manufacturers and other firms that depend on global supply chains.
- As many as 18,000 of SolarWind’s corporate customers were placed in jeopardy by a malicious software update, including Fortune 500 firms and U.S. government agencies, according to Business Insider.
- In the months that the malware remained undetected on these networks, hackers were able to destroy and alter critical data and impersonate business and government officials.
Cybersecurity professionals are taking the fight to the crooks as they redouble their efforts to protect against ransomware and other supply chain attacks. Governments and private companies are adopting the same international collaboration to fight ransomware as is used to combat organized crime, terrorism, and global human trafficking networks.
This guide summarizes the efforts underway to catch and prosecute the international criminal gangs perpetrating ransomware and to prevent future ransomware attacks on the global supply chain.
What Is a Supply Chain Attack?
A supply chain attack breaks into the victim’s network by taking advantage of vulnerabilities in the computer systems of the company’s supply chain partners. The attacks are an attempt to infiltrate an organization’s computers to gain access to the networks of its many suppliers and partners. SecurityWeek describes such attacks as “hub and spokes” because by compromising one company, the criminals gain access from that hub to the firm’s partners via network connections serving as spokes.
Supply chains are perceived as especially vulnerable to ransomware attacks due to the broad targets they represent and the opportunity to cause large-scale damage via a single exploited vulnerability.
- The COVID-19 pandemic contributed to the increase in ransomware attacks on supply chains by creating millions of potential access points as companies moved to remote working.
- Small firms are particularly susceptible to supply chain attacks because they lack the resources to implement the security required to prevent them, according to SecurityWeek.
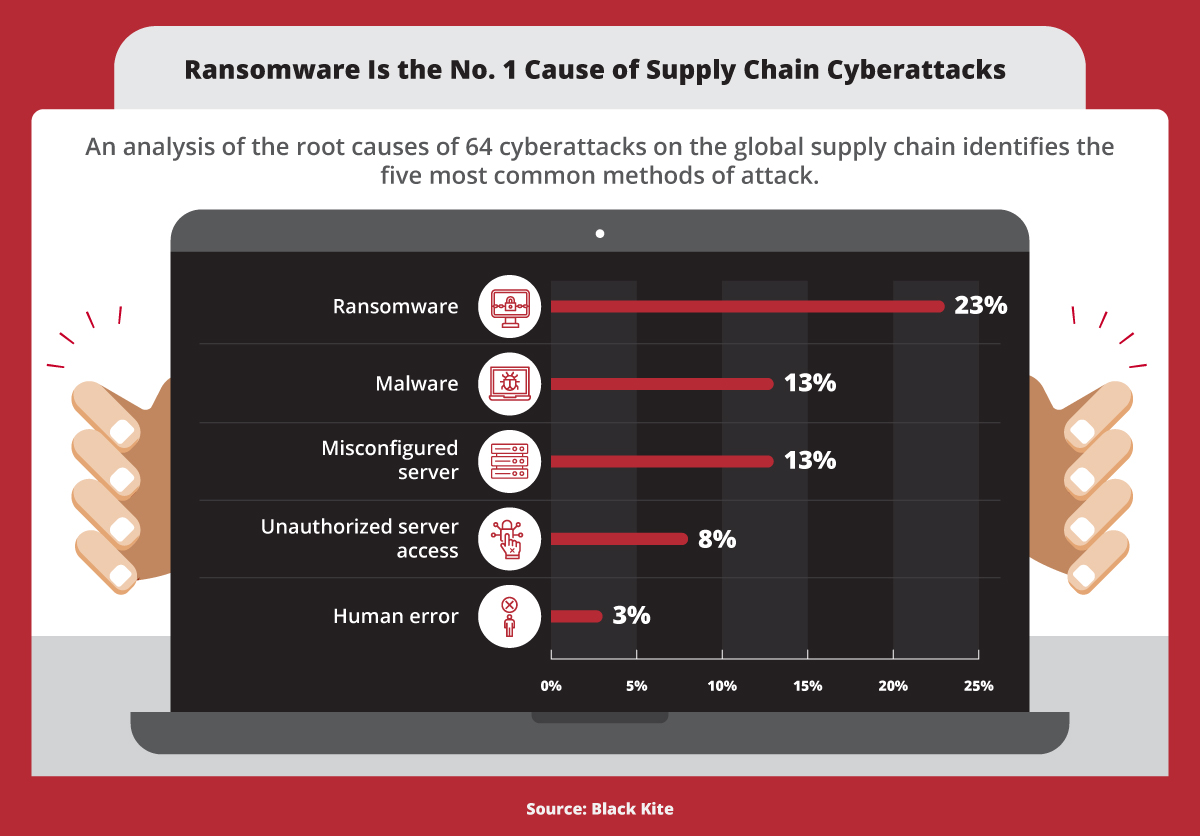
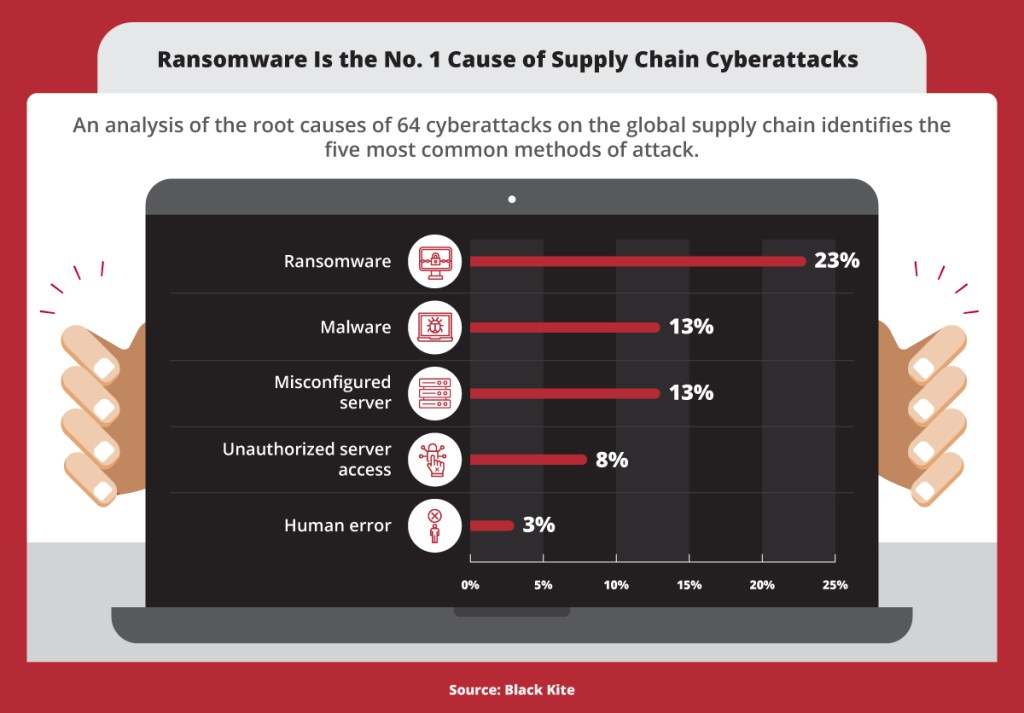
The root causes of 64 cyberattacks on the global supply chain identifies the five most common methods of attack, according to Black Kite. 1. Ransomware: 23%. 2. Malware: 13% 3. Misconfigured server: 13%. 4. Unauthorized server access: 8%. 5. Human error: 3%.
Techniques Used by Cybercriminals to Attack the Supply Chain
Among the methods used by ransomware purveyors and intellectual property thieves to attack supply chains are social engineering (also called phishing), “malvertising,” and leveraging software vulnerabilities:
- Social engineering and phishing trick people into opening and downloading an infected file by pretending to be from a known or trusted party, such as a boss or co-worker.
- Malvertising infects an iframe or invisible element on a webpage or other HTML element, which redirects to a page that downloads an infected file and executes malicious code without the person being aware.
- Vulnerabilities in software code allow ransomware such as WannaCry to infect computers on a network without the victim having to take any action. WannaCry is a worm that spreads from PC to PC, encrypting the user’s files and demanding a ransom to decrypt them. The vulnerability that WannaCry leveraged to load ransomware on victims’ computers starting in 2017 had been patched months earlier, but organizations that hadn’t applied the necessary software patch remained vulnerable to the attack. The ransomware has infected thousands of computers and continues to infect vulnerable PCs. While individual ransom demands are in the hundreds of dollars, WannaCry’s overall damage is estimated to have reached billions of dollars.
A report by the Cybersecurity and Infrastructure Security Agency (CISA) identifies several recent trends in ransomware supply chain attacks:
- The criminals behind the attacks are sharing the information they steal from victims with other criminals and sharing access to the compromised networks.
- The attacks are attempting to do greater damage by targeting cloud resources, industrial processes, and the software supply chain, all of which involve large, complex networks.
- The crimes are more likely to occur on weekends and holidays, when IT staffing is low and alerts are less likely to be noticed and responded to appropriately.
Supply Chain Security’s Weak Link: Managed Service Providers
Managed service providers (MSPs) and managed security service providers (MSSPs) have been the sources of many breaches of supply chain security. The Internet Crime Complaint Center (IC3) warns that because of their trusted status with their clients, MSPs and MSSPs are becoming favorite targets of ransomware attacks.
This was the case with SolarWinds, whose Orion system management software was used by thousands of large enterprises, organizations, and government agencies. More than 18,000 Orion users installed a malicious software update, which remained undetected for months. The criminals attacking SolarWinds were able to access the data and networks of thousands of partners of the organizations using Orion. While the purpose of the attack is uncertain, the perpetrators are believed to be the Russian Foreign Intelligence Service.
A survey by security firm Kaspersky found that 98% of the MSPs affected by the ransomware attack on SolarWinds responded by strengthening their security measures. These are the actions the MSPs took most often:
- Switching to another IT security software vendor (44%)
- Updating the terms of contracts with suppliers that relate to liability (42%)
- Hiring more IT security professionals (39%)
- Acknowledging the need to hire a risk management expert (35%)
MSPs that heard of the SolarWinds attack but weren’t directly affected by it were most likely to adopt new security solutions (32%), hire more IT security professionals (27%), spend more on IT security training (23%), and update internal data security policies (22%).
What Is Behind the Recent Surge in Ransomware Supply Chain Attacks?
Ransomware attacks continue to increase in the overall number of attacks and in the severity of the damage these breaches do to organizations. Financial gain and political goals are the primary motivations of supply chain attacks. AT&T lists five reasons for the increase in ransomware attacks on supply chains:
- Victims are more willing to pay the ransom.
- Rising international tensions create political animosity that leads to cyber warfare.
- The number of potential access points for ransomware increases as organizations expand their networks to support remote workers and partners.
- Cryptocurrency allows the payment of ransoms to cybercriminals who can remain anonymous.
- Criminals now offer ransomware as a service, so criminals with no technical expertise can launch the attacks.
CISA notes that cybercriminals’ ransomware attacks now target critical infrastructure more frequently. These are the industries that are most likely to encounter ransomware, according to CISA:
- Communications
- Emergency water services
- Energy
- Financial services
- Healthcare
Risks of Supply Chain Cyberattacks
The impact of ransomware attacks on organizations can be devastating beyond their financial costs. In the past, companies were inclined to pay the ransoms and get back to business as quickly as possible, but in 2022 they face a backlash from the public for giving in to criminals, Forbes reports.
The Office of Foreign Assets Control (OFAC) of the U.S. Department of the Treasury warns companies that they could face sanctions for facilitating ransomware transactions. In addition to losing the trust of the public, firms that pay ransoms to cybercriminals could face lawsuits for failing to protect the public from the damages they suffer as a result of the cyberattacks.
The Data and Digital Resources Targeted by Supply Chain Attacks
The one thing all ransomware supply chain cyberattacks have in common is they’re all after data of some kind. The criminals’ purpose may be financial gain and/or political power, but the tool they use to capitalize on the attack is data.
In defending against ransomware attacks, organizations must match each type of data to the most secure and efficient medium for storing that data, as InfoSecurity Magazine points out:
- An organization’s most sensitive data may need to reside in-house, where the company’s firewall secures it.
- Communications with and data transfers between supply chain partners must be encrypted end to end, and audits may be required to confirm that partners are following security best practices in their storage and use of the data.
- As enforcement efforts are stepped up to meet the growing ransomware threat, cybercriminals are expected to target supply chain data that isn’t sufficiently protected (low-hanging fruit) rather than try to break through layers of data security.
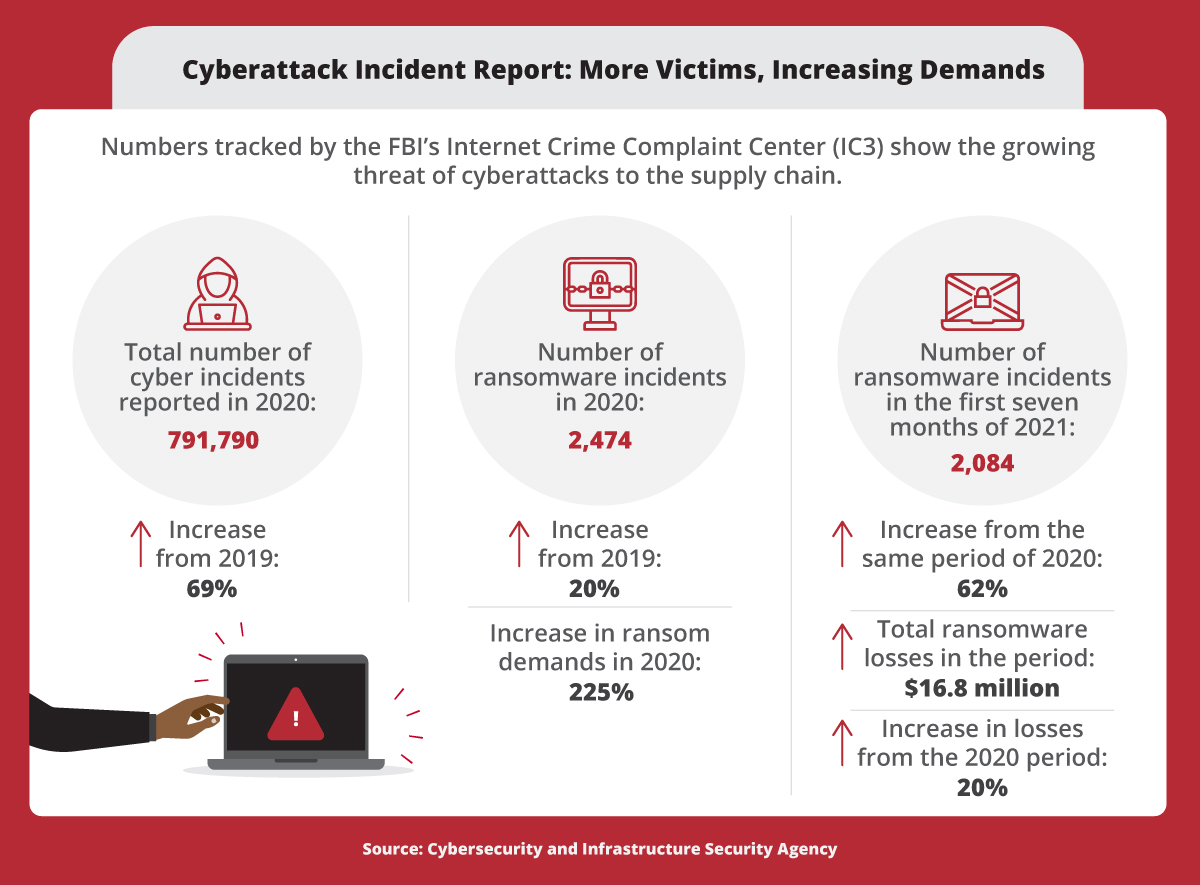
The threat of cyberattacks to the supply chain is growing, according to numbers tracked by the FBI’s Cybersecurity & Infrastructure Security Agency Internet Crime Complaint Center (IC3). Total number of cyber incidents reported in 2020: 791,790 (increase from 2019: 69%). Number of ransomware incidents in 2020: 2,474 (increase from 2019: 20%; increase in ransom demands in 2020: 225%). Number of ransomware incidents in the first seven months of 2021: 2,084 (increase from the same period of 2020: 62%; total ransomware losses in the period: $16.8 million; increase in losses from the 2020 period: 20%).
Financial Costs of Supply Chain Cyberattacks
The damage done by attacks on the supply chain is widespread. In addition to the financial costs of cyberattacks to organizations, the crimes negatively affect a company’s relationships with business partners and customers. American Global Logistics examines the many risks entailed in securing supply chains from the threat of ransomware attacks.
- The attacks can disrupt many different aspects of an organization’s operations, resulting in lower sales, lower revenue, and lower profit.
- The bad press resulting from the attacks can do serious damage to a company’s brand.
- Shareholders may have reason to question the soundness of their investment in the firm.
Among the companies that have paid or are believed to have paid ransoms after having their supply chains infiltrated by criminals include the German chemical firm Brenntag, which paid a $4.4 million ransom to the ransomware gang DarkSide, and Colonial Pipeline, which also paid a $4.4 million ransom to the group.
Resources on the Risks of Supply Chain Cyberattacks
- Check Point, 2022 Interactive Cyber Security Report — This report, which requires registration to access, provides a timeline of major cybersecurity events in 2021 as well as analyses of five cybersecurity trends.
- Forbes, “Software Supply Chains and Enterprise IoT Will Be Big Attack Targets in 2022” — Among the cybersecurity predictions for 2022 is that software supply chains will be limited to the handful of nation-states able to muster the sophisticated techniques required to infiltrate the software development process.
- VentureBeat, “Cybersecurity’s Challenge for 2022 Is Defeating Weaponized Ransomware” — This article points out that ransomware attackers are developing ways to bring down entire supply chains by using vulnerability chaining, which takes advantage of multiple software vulnerabilities in a single attack.
Supply Chain Attack Examples
In 2021, ransomware was a component of 10% of all data breaches, more than twice the number recorded in 2020, according to the Verizon Data Breach Investigations Report. IDC’s 2021 Ransomware Study found that 37% of global organizations were victims of ransomware attacks, as TechTarget reports.
- In 90% of the ransomware attacks in 2021, the company targeted suffered no financial loss, according to the Verizon report.
- When such an attack did cause a financial loss for a large organization, the median amount of the loss was $11,500.
- In 95% of ransomware attacks, the range of financial losses was between $70 and $1.2 million.
The high number of failed ransomware attacks may indicate that more companies are refusing to pay, although it can also be because firms are not reporting the loss of customer data as financial. The Verizon report speculates that companies may be underreporting the number of ransomware attacks they’ve been subject to.
These are among the most damaging ransomware supply chain attacks:
SolarWinds
Many companies use the SolarWinds Orion Platform to manage their IT systems, but a routine software update in March 2020 contained malware that security analysts believe the Russian intelligence service, SVR, planted. The hackers had gained access to the SolarWinds network starting in September 2019.
TechTarget reports that more than 18,000 SolarWinds customers downloaded and installed the malware-infested update, which allowed the attackers to access the firms’ computer networks and install even more malware. In December 2020, the security firm FireEye announced that it was the victim of a nation-state attack, and days later determined that the supply chain attack was the result of “trojanizing” the SolarWinds Orion Platform.
It’s estimated that government agencies and private companies may spend as much as $100 billion to recover from the SolarWinds ransomware attack.
Kaseya
Virtual systems administration software vendor Kaseya was attacked by the REvil ransomware in July 2021, resulting in more than 2,000 Kaseya customers around the world having their systems compromised. Executives at Kaseya had been warned as far back as 2017 of the software vulnerabilities that were leveraged in the attack, according to Bloomberg.
In November 2021, the U.S. Department of Justice announced that it had arrested a Ukrainian national and a Russian national, charging them both with instigating the Kaseya ransomware attack. U.S. officials also seized more than $6 million in ransom payments related to the case.
Accellion
File transfer vendor Accellion initially announced that it had been hit by a cyberattack in December 2020 and that it had patched the vulnerability. However, days later the company was forced to admit that several other vulnerabilities remained, and it wasn’t until March 2021 that a complete patch of its systems was made available.
More than six months after the initial attack, more victims continued to be discovered, including the financial firm Morgan Stanley, which lost an unknown number of documents containing sensitive customer information. Other victims included an Arkansas-based healthcare service and the University of California, Berkeley.
Codecov
Much like the SolarWinds ransomware attack, the malware that infected the distribution network of software testing vendor Codecov remained undetected for several months. The company announced that the attackers gained access to its network on Jan. 31, 2021, but the intrusion wasn’t discovered until April 1, 2021.
Analysts estimate that the ransomware affected hundreds of Codecov’s 29,000-plus customers, which include large firms such as GoDaddy, Procter & Gamble, and The Washington Post. The information that the attackers stole included customer credentials that allowed them to access hundreds of client networks. The credentials could provide the criminals with access to thousands of other restricted systems, according to investigators.
JBS
In June 2021, the Brazilian company JBS, the largest meat processor in the world, announced that it had paid a ransom of $11 million in Bitcoin after a group of hackers that the FBI believed to be the Russian-based group REvil attacked it. The ransomware attack had shut down the company’s U.S. beef plants and disrupted its pork and poultry operations. JBS stated that it paid the ransom to avoid losing vital information and compromising sensitive customer data.
JBS discovered the attack on May 30, 2021, after it had infected its IT systems in North America and Australia. Four days after the discovery, the firm had fully restored all its networks. The company claims that none of its data or customer data was lost as a result of the breach.
Resources on Global Supply Chain Attacks
- eSecurity Planet, “SolarWinds-Like Supply Chain Attacks Will Peak in 2022, Apiiro Security Chief Predicts” — While the number of ransomware attacks on supply chains will likely increase in the year, companies are also improving their defenses against such attacks, according to Moshe Zioni, vice president of security research at Apiiro.
- Office of the Director of National Intelligence, Supply Chain Risk Management — Reports and research findings are presented relating to supply chain risk management policies, standards, and best practices.
- Microsoft, “Supply Chain Attacks” — A video of the mechanics of a software supply chain attack and tips for software developers and vendors to help defend against attacks are provided.
Supply Chain Attack Prevention for Organizations
To stay ahead of the criminals, cybersecurity professionals need to constantly develop new approaches to prevent supply chain attacks as well as to mitigate their damage. In May 2021, President Biden issued an executive order on improving the nation’s cybersecurity that calls for enhancing software supply chain security by developing guidelines in three areas:
- Securing software development pipelines
- Auditing trust relationships
- Monitoring operations and alerts to speed responses to cyberattacks
Even as ransomware supply chain attacks become more prevalent and sophisticated, organizations can take steps to reduce the risk of victimization. The first step in supply chain attack prevention is to audit existing defense methods to determine their reliability and identify gaps in security coverage.
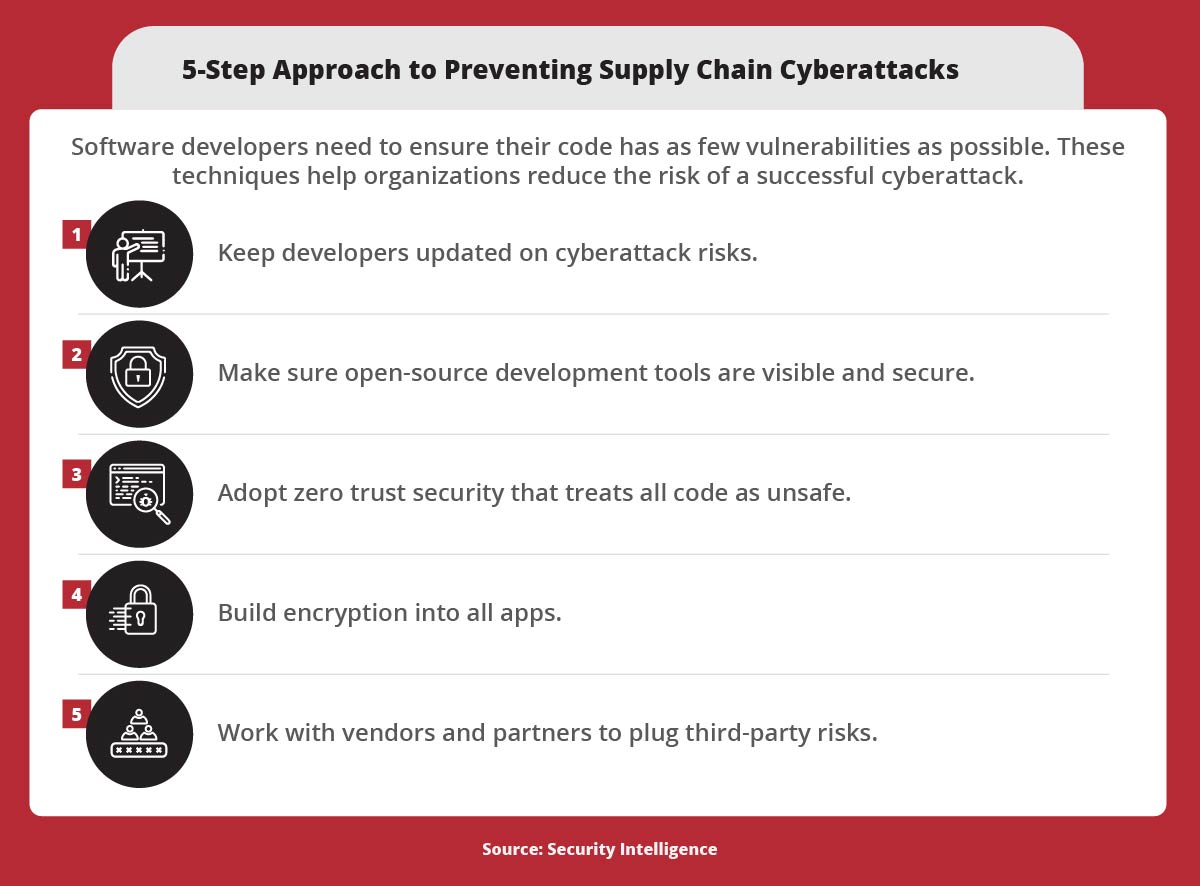
Software developers need to ensure their code has as few vulnerabilities as possible. These techniques help organizations reduce the risk of a successful cyberattack, according to Security Intelligence: 1. Keep developers updated on cyberattack risks. 2. Make sure open-source development tools are visible and secure. 3. Adopt zerotrust security that treats all code as unsafe. 4. Build encryption into all apps. 5. Work with vendors and partners to plug third-party risks.
Techniques for Preventing Supply Chain Cyberattacks
Supply chain software needs to be more visible so the quality of supply chain security is known to the public. Stopping attacks on the supply chain requires that software ships with no vulnerabilities cybercriminals can exploit. These are among the steps that supply chain software vendors and their customers must take:
- Identify and plug third-party data leaks.
- Lock down internal systems and vendor networks by patching all known vulnerabilities.
- Evaluate partners’ security measures and vendors’ security ratings.
Tools and approaches to achieve these goals include the following:
- “Honeytokens” are fake data resources planted on a company’s network to attract attackers and alert the company about suspicious activity. In addition to providing advanced notice of an attack, honeytokens indicate the methods the attackers will use and can sometimes identify the criminal parties.
- Privileged access accounts must be managed carefully by implementing a privileged access management (PAM) platform that disrupts the path from initial network access to exfiltration of sensitive data.
- Cybercrime awareness training instructs staff on how to detect a phishing attempt, how to protect their login credentials, and how to identify and report breach attempts.
- Third-party data leak detection tools prevent ransomware attacks that originate on vendor and partner networks, even when the third party is unaware of the breach.
- Encryption of all internal data is one of the simplest ways to discourage cybercriminals, who often prefer to attack systems that are easily breached. Encryption should meet the Advanced Encryption Standard (AES).
- Zero Trust architecture (ZTA) is a security approach that assumes all activity on the company’s network is malicious by default, so access to sensitive information requires that each connection request meet a stringent set of security policies.
- Multiple layers of defense integrate antivirus, multifactor authentication, and attack surface monitoring, among other data security measures. Multilayer security creates operational layers, each of which has unique capabilities and functions targeted at preventing a specific type of threat.
Resources on Supply Chain Attack Prevention
- Cybersecurity and Infrastructure Security Agency, Defending Against Software Supply Chain Attacks — The document explains software supply chain risks, attack approaches, and methods for identifying and patching vulnerable software.
- CyberTalk.org, 10 Extremely Effective Ways to Prevent Supply Chain Attacks — The techniques described include conducting a risk assessment, using least privilege access (giving all users access to only the privileges they need for each individual task they perform), segmenting networks, and integrating security into the software development life cycle.
The Worldwide Battle Against Cybercriminals
The work being done in organizations and by government agencies to thwart ransomware, information theft, and other attacks on the global supply chains promises to reduce the risk of supply chain disruptions, despite the expected increase in ransomware attempts. Cybersecurity professionals who are trained in the latest approaches to keeping sensitive data safe are leading the efforts underway to make the supply chain more resilient and less susceptible to attack. More resilient and more reliable global supply chains benefit manufacturers, consumers, and the economies of nations around the world.
Infographic Sources
Black Kite, “The Most Common Cybersecurity Threats Facing Supply Chains in 2021”
Security Intelligence, “5 Ways to Defend Against Supply Chain Cyberattacks”
U.S. Federal Bureau of Investigation, “Ransomware Awareness for Holidays and Weekends”

