How to Prevent Cyberattacks: Top Ways to Protect Yourself
According to a 2020 Verizon report, 86% of global data breaches are financially motivated. Now more than ever, individuals and businesses must proactively maintain their cybersecurity because the cost of a cyberattack can run well into the millions — a price few are able or willing to pay.
To learn more, check out the infographic below, created by Maryville University’s Online Bachelor of Science in Cybersecurity program.
Add This Infographic to Your Site
<p style="clear:both;margin-bottom:20px;"><a href="https://online.maryville.edu/blog/how-to-prevent-cyber-attacks/" rel="noreferrer" target="_blank"><img src="https://online.maryville.edu/wp-content/uploads/sites/97/2021/03/MVU-BSCS-2020-Q3-IG-How-to-Prevent-Cyber-Attacks-Top-Ways-to-Protect-Yourself-final.png" alt="Cybersecurity statistics and information on how to prevent cyber attacks" style="max-width:100%;" /></a></p><p style="clear:both;margin-bottom:20px;"><a href="https://online.maryville.edu" rel="noreferrer" target="_blank">Maryville University </a></p>Cybersecurity vulnerabilities
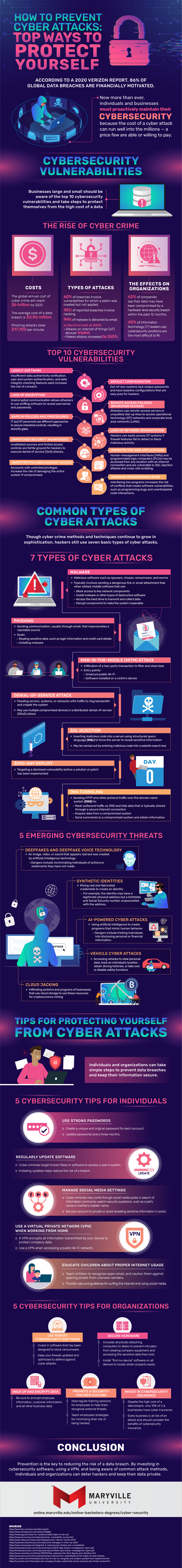
Businesses large and small should be aware of the top 10 cybersecurity vulnerabilities and take steps to protect themselves from the high cost of a data breach.
The rise of cybercrime
Cybercrime is expensive. The average cost of a data breach is $3.86 million, with the global annual cost of cybercrime estimated to reach $6 trillion by 2021. Phishing attacks, for example, steal a jaw-dropping $17,700 per minute.
Hackers use a variety of techniques, but trends are revealing which tactics they prefer. Six out of 10 breaches involve vulnerabilities for which a patch was created but not applied, while 45% of reported breaches involve hacking and 94% of malware is delivered by email.
In the first half of 2019, attacks on internet of things (IoT) devices tripled and fileless attacks increased by 265%.
Organizations of all sizes are being affected by data breaches, with 63% of companies saying their data may have been compromised by a hardware-level security breach within the past 12 months. Some 40% of information technology (IT) leaders say cybersecurity positions are the most difficult to fill.
Top 10 cybersecurity vulnerabilities
Businesses should be aware of the most common cybersecurity vulnerabilities; these include legacy software, default configuration, lack of encryption, remote access policies (backdoor access), gaps in policies and procedures, lack of network segmentation, unpatched security weaknesses, unprotected web applications, unrestricted user account access, and unknown programming bugs.
Common types of cyberattacks
Though cybercrime methods and techniques continue to grow in sophistication, hackers still use seven basic types of cyberattacks.
7 types of cyberattacks
During a malware attack, a hacker sends a dangerous link or email attachment that, when clicked, installs software that can block access to key network components, install malware or other types of destructive software, access the hard drive to transmit and collect data, and disrupt components to make the system inoperable.
A phishing attack involves sending communication, usually through email, that impersonates a reputable source. The goals of this attack may be to steal sensitive data, such as login information and credit card details, and to install malware.
A man-in-the-middle (MitM) attack occurs when a hacker infiltrates a two-party transaction with the intent to filter and steal data. Common entry points for this type of attack include unsecure public Wi-Fi and software installed on a victim’s device.
During a denial-of-service attack, a bad actor floods servers, systems, or networks with traffic to clog bandwidth and cripple the system. This type of attack may use multiple compromised devices in a distributed-denial-of-service (DDoS) attack.
An SQL injection involves inserting malicious code into a server using structured query language (SQL) to force the server to reveal sensitive information. The cybercriminal may enter malicious code into a website search box to carry out this type of attack.
A zero-day exploit attack involves targeting a disclosed vulnerability before a solution or patch has been implemented. Organizations that fail to act quickly may find themselves the target of this type of attack.
DNS tunneling occurs when a bad actor sends HTTP and other protocol traffic over the domain name system (DNS) to mask outbound traffic as DNS and hide data that is typically shared through a secure internet connection; acquire data from a compromised system; and send commands to a compromised system and obtain information.
5 emerging cybersecurity threats
Deepfakes and deepfake voice technology use artificial intelligence technology to create an image, video, or sound that appears real. The dangers of this threat include incriminating individuals of actions or statements they have not made.
A similar cybersecurity threat is the mixing of real and fabricated credentials to create a synthetic identity. For example, the identity may have a legitimate physical address but a birthdate and Social Security number unassociated with the address.
AI-powered cyberattacks use artificial intelligence to create programs that mimic human behavior.
When successful, this type of attack can trick individuals into disclosing personal or financial information.
Vehicle cyberattacks may involve accessing vehicles to steal personal data, track an individual’s location, obtain driving histories, or take over or disable safety functions.
Cybercriminals may also engage in cloud jacking by infiltrating systems and programs of businesses that use cloud storage to use these resources for cryptocurrency mining.
Tips for protecting yourself from cyberattacks
Individuals and organizations can take simple steps to prevent data breaches and keep their information secure.
5 cybersecurity tips for individuals
The first and most basic step in maintaining cybersecurity is to create a unique and original password for each account. Users should also remember to update passwords every three months.
Keeping up with software updates is important, as cybercriminals often target known flaws in software to access a user’s system.
Cybercriminals may comb through social media posts in search of information commonly used in security questions, such as a pet’s name or mother’s maiden name. To combat this risk, social media users should set their account to private or avoid revealing sensitive information in posts.
A virtual private network (VPN) is a great way to protect sensitive data, especially when accessing a public Wi-Fi network. A VPN encrypts all information transmitted by your device and helps prevent many types of cyberattacks.
And finally, teachers and parents should educate children about proper internet usage. Children and teens should know what the rules and guidelines are for surfing the internet and using social media.
5 cybersecurity tips for organizations
To protect business data, it’s important to secure hardware, back up and encrypt data, invest in cybersecurity insurance, promote a security-focused culture, and use robust cybersecurity software. Taking these steps will help reduce risk and keep the business operating without interruption.
Reducing risk
Prevention is the key to reducing the risk of a data breach. By investing in cybersecurity software, using a VPN, and being aware of common attack methods, individuals and organizations can deter hackers and keep their data private.
Sources
Cisco, “What Are The Most Common Cyber Attacks”
Compuquip, “Top 9 Cybersecurity Threats And Vulnerabilities”
CSO Online, “Top Cybersecurity Facts, Figures and Statistics”
Cybercrime Magazine, “Cybercrime To Cost The World $10.5 Trillion Annually By 2025”
Dell Technologies, “BIOS Security — The Next Frontier for Endpoint Protection”
Entrepreneur, “Five Ways To Protect Your Company Against Cyber Attacks”
F-Secure, “Attack Landscape: H1 2019”
Norton, “11 Ways to Help Protect Yourself Against Cybercrime”
Norton, “Cyberthreat Trends: 15 Cybersecurity Threats For 2020”
RiskIQ, “The Evil Internet Minute 2019”
ServiceNow, “Costs and Consequences of Gaps in Vulnerability Response”

